There are two ways to administer Splunk: using Splunk web interface, which is normally done by most administrators, or by using configuration files. Each way has its own pros & cons.
In this post, we’ll talk about Splunk configuration files, which are created for you automatically even when you administer Splunk using Web Interface.
Knowing how to configure Splunk using configuration files will help explain certain issues you might face when configuring Splunk using Web Interface.
What are Splunk Configuration Files?
A Splunk configuration file is an ascii file containing information about the object being managed by Splunk. For instance, all saved searches and alerts in Splunk are saved in a configuration file called “savedsearches.conf”. Where this configuration file is stored in the hierarchy determines who can access the saved searches and alerts defined in this configuration file.
There are multiple examples of configuration files in Splunk and each serves a defined purpose, and we’ll cover them later in this post.
The Benefits of Splunk Configuration Files vs Splunk Web Interface
As mentioned earlier, you can administer Splunk using web Interface or using configuration files. Using web interface is much easier, but lacks the flexibility and options that can further customize the functionality required when using configuration files. This leads us to the benefits of using Splunk Configuration files.
In the following section, I’ll show you a few benefits of using Splunk configuration files.
Benefit # 1
We can use Splunk web to ingest all logs in a specific folder, which will create the configuration file needed (inputs.conf) and ingests all logs in that folder.
However, if we wanted to ignore logs that are older than 7 days, will need to add the option in the inputs.conf (ignoreOlderThan = 7d), which can only be done using configuration files.
Benefit # 2
In the example of saving searches in Splunk, if we were using Splunk web, by default Splunk will create a savedsearches.conf in the same application context we are at within Splunk, so when we change our context to another application, the saved search can’t be seen.
However, if we saved the search using configuration files and placed the file globally, will be able to access the saved search globally.
Splunk has a long list of configuration files, in the next section will provide a list of the most useful ones and their purpose.
List of Splunk Configuration Files
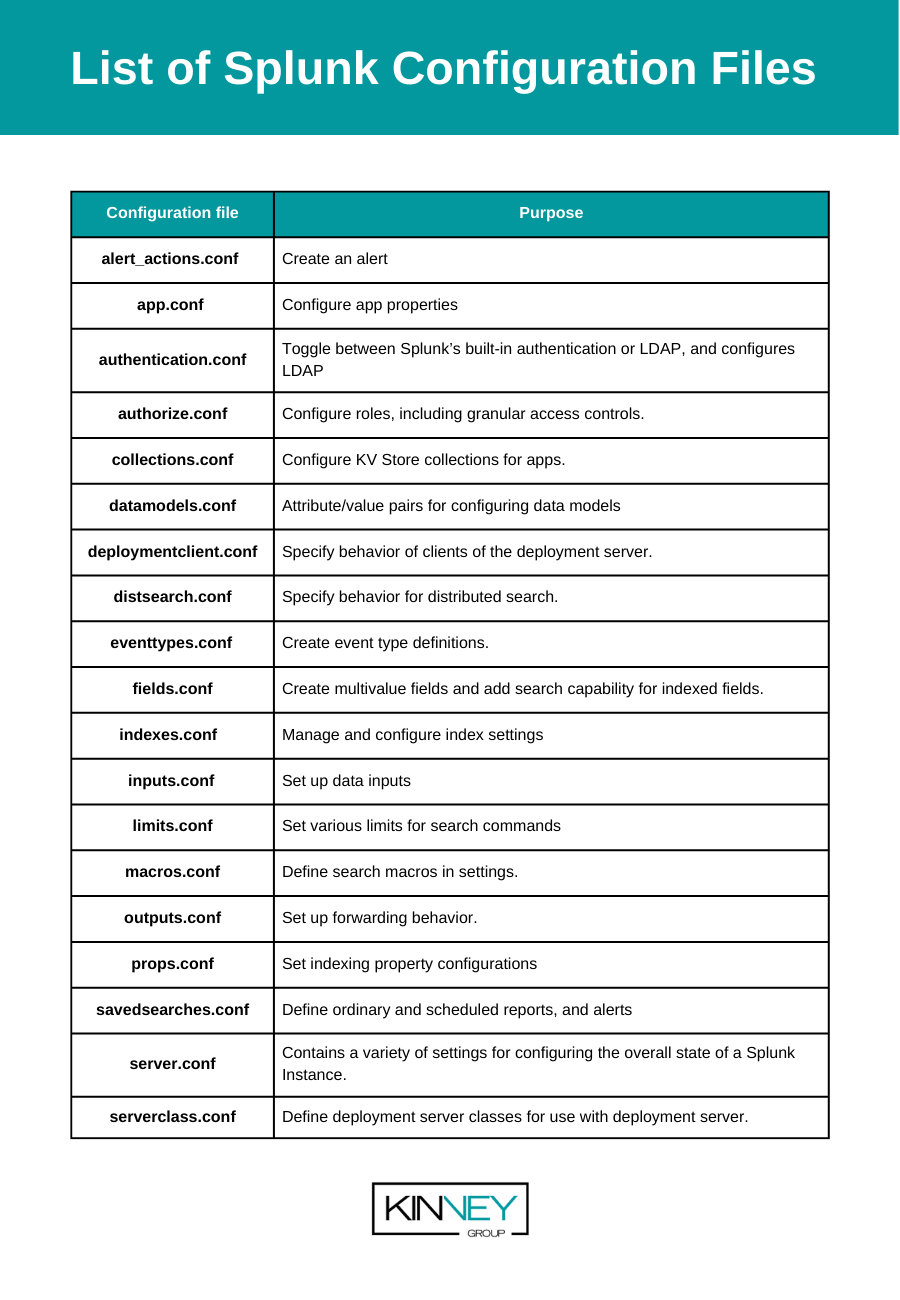
| Configuration file | Purpose |
| alert_actions.conf | Create an alert |
| app.conf | Configure app properties |
| authentication.conf | Toggle between Splunk’s built-in authentication or LDAP, and configures LDAP |
| authorize.conf | Configure roles, including granular access controls. |
| collections.conf | Configure KV Store collections for apps. |
| datamodels.conf | Attribute/value pairs for configuring data models |
| deploymentclient.conf | Specify behavior of clients of the deployment server. |
| distsearch.conf | Specify behavior for distributed search. |
| eventtypes.conf | Create event type definitions. |
| fields.conf | Create multivalue fields and add search capability for indexed fields. |
| indexes.conf | Manage and configure index settings |
| inputs.conf | Set up data inputs |
| limits.conf | Set various limits for search commands |
| macros.conf | Define search macros in settings. |
| outputs.conf | Set up forwarding behavior. |
| props.conf | Set indexing property configurations |
| savedsearches.conf | Define ordinary and scheduled reports, and alerts |
| server.conf | Contains a variety of settings for configuring the overall state of a Splunk Instance. |
| serverclass.conf | Define deployment server classes for use with deployment server. |
Conclusion
Configuration files in Splunk are used and created to administer Splunk when using Splunk Web Interface. Certain functionalities can not be administered by Splunk Web only, modifications to Configuration files are required.
If you found this helpful…
You don’t have to master Splunk by yourself in order to get the most value out of it. Small, day-to-day optimizations of your environment can make all the difference in how you understand and use the data in your Splunk environment to manage all the work on your plate.
Cue Atlas Assessment: Instantly see where your Splunk environment is excelling and opportunities for improvement. From download to results, the whole process takes less than 30 minutes using the button below:





