
Where to begin with Splunk eval search command… in its simplest form, eval command can calculate an expression and then applies the value to a destination field. Although, that can be easier said than done. That’s why in this post, we’ve broken down the eval command so you can understand exactly what it is, what it does, and why it’s so valuable to Splunkers everywhere.
What is the eval command in Splunk?
The eval command is a commonly used command in Splunk that calculates an expression and applies that value to a brand new destination field.
Eval command is incredibly robust and one of the most commonly used commands. However, you probably don’t know all the possibilities eval is capable of performing. Before we jump right in, let’s take a quick look at the syntax:
Eval Command Syntax
|eval <field> = <expression>
What does the eval command do?
Essentially, you are creating a field in Splunk where one doesn’t already exist. The primary benefit of the eval command is that it allows you to see patterns in your data by putting the data into context. That context is created through various formulas that carry out specific functions such as:
- Mathematical functions
- Comparison functions
- Conversion functions
- Multivalue functions
- Date and Time functions
- Text functions
- Informational functions
Each of the functions above has its own list of arguments-based functions, but in this guide, we’ll start with ways to use some basic eval commands.
Ways to Use the eval Command in Splunk
1. Use the eval command with mathematical functions
When we call a field into the eval command, we either create or manipulate that field for example:
|eval x = 2
If “x” was not an already listed field in our data, then I have now created a new field and have given that field the value of 2. If “x” is a field within our data, then I have overwritten all the fields so that now x is only 2. This is the simplest way to use eval, list a field, and give it a value.
Although it might seem too simple to list here, using eval to complete mathematical functions can be quite helpful when analyzing a lot of data. You can turn values into percentages and even use the stats command to add additional context to your data.
|stats count |eval number = 10 |eval percent = (count/number)*100
2. Format time values with the eval command.
There are a couple of ways we can work with time using eval.
The first is formatting. Here’s an example: If we are bringing in a time field but it’s written in epoch time, we can convert it into a readable time format:
|eval time = strftime(<time_field>, “%Y-%m-%d %H:%M:%S”)
The second is stripping a time format and converting it to epoch:
|eval time= strptime(<time_field>, “%Y-%m-%d %H:%M:%S”)
I know what you’re thinking, “That’s cool, but what if I need to compare my time values with a static time value to say, I don’t know, filter out events”? Great question, here’s how to do that.
3. Compare time values with eval
Using “relative-time” I can create a rolling time window:
|eval month = relative_time(now(), “-1mon”)
This line will return a value that is exactly 1 month from now, the time period can be changed to be a day, a week, 27 days, 4 years, whatever your heart desires. From here we can use a where command to filter our results:
|eval time= strptime(<time_field>, “%Y-%m-%d %H:%M:%S”) |eval month = relative_time(now(), “-1mon”) |where time > month
Because both of these time values are in epoch, we can simply find results where time is a higher number than a month, or in even simpler terms, anything more recent than one month.
4. Use If and Case with eval
IF and CASE are in the same vein of comparison, however, CASE will allow for more arguments. Let’s take a quick look at these two:
|eval test = if(status==200, “Cool Beans”, “No Bueno”)
Using IF
Here’s the breakdown, when using IF, we need to pass three arguments:
- The condition – this is usually “if something equals some value”
- The result – if said field does equal the defined value, then the test’s value is the argument
- The else – if said field does NOT equal the defined values, then test’s value is the argument
In this case, if status equals 200, then the text would say, “Cool Beans.” If the value of status is anything other than 200, then the text reads, “No Bueno.”
Using CASE
As stated earlier, CASE will allow us to add more arguments…
|eval test = case(status==”2*”, “Cool Beans”, status==”5*”, “Yikes”, status==”4*”, “might be broken”)
As you can see, we can apply multiple conditions using the case to get a more robust list of descriptions.
5. Use lower/upper with eval.
Sometimes, the text formatting in our data can be weird. Splunk says that when you search for a value it doesn’t need to be case-sensitive… but take that with a grain of salt. It’s also not true when comparing values from different sources. Check out this scenario…
Event Data – ID: 1234AbCD
Lookup – ID: 1234abcd
If I’m trying to use a lookup command and join and get values in a coherent table of information, that’s not going to happen. Why? Because the two values don’t match. Sure, the numbers and letters are the same, but the formatting is different. Splunk views that as a roadblock. Need a quick fix? Here’s one that’s super easy and barely an inconvenience.
|eval id = lower/upper(id)
Lower and upper will allow you to format a field value to make all letters each lowercase or uppercase depending on which function you use. Finally, make the letters in the event data lowercase so that the lookup and indexed data can communicate correctly.
Splunk Pro Tip: There’s a super simple way to run searches simply—even with limited knowledge of SPL— using Search Library in the Atlas app on Splunkbase. You’ll get access to thousands of pre-configured Splunk searches developed by Splunk Experts across the globe. Simply find a search string that matches what you’re looking for, copy it, and use right in your own Splunk environment. Try speeding up your eval command right now using these SPL templates, completely free.
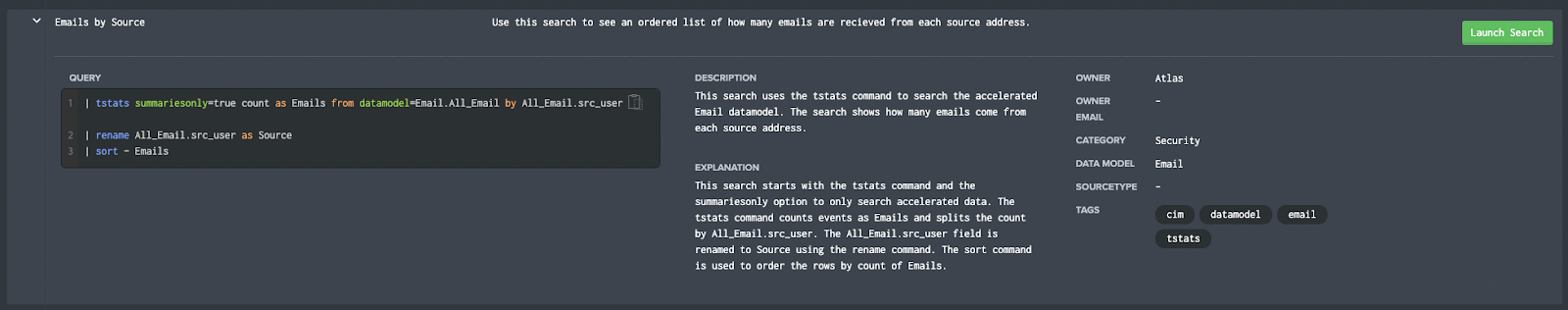
Run a pre-Configured Search for Free
Other eval functions
Lower(x)
Lower will take all the values from a field and make them lowercase
Syntax:
|eval field = lower(field)
Upper(X)
Upper will do the same as lower but all uppercase
Syntax:
|eval field = upper(field)
Typeof(x)
Typeof will create a field that will tell you the data type of the field.
Syntax:
|eval type = typeof(field)
Example: string, number
Round(X,Y)
Round will take a numeric value and round it to the nearest defined decimal place
Syntax
| eval field = round(field, decimal place)
Example – round(4.56282,2) = 4.56
Mvjoin(x,y)
This will take a field that has multiple values separated by a space and add a delimiter making it a single value (think opposite of makemv)
Syntax:
|eval field = (field,string) |eval field = mvjoin(field, “,”)
Output = 1,2,3,4,5
Example: Field – number = 1 2 3 4 5
Eval Command Basics
Eval is a very powerful command in Splunk that gives you insight into your data that just can’t be seen on the surface of your monitoring console dashboards. Try out the eval command on your next search and explore the possibilities for yourself.
If you found this helpful…
You don’t have to master Splunk by yourself in order to get the most value out of it. Small, day-to-day optimizations of your environment can make all the difference in how you understand and use the data in your Splunk environment to manage all the work on your plate.
Cue Atlas Assessment: a customized report to show you where your Splunk environment is excelling and opportunities for improvement. Once you download the app, you’ll get your report in just 30 minutes.





