Have you ever been stuck with a single field that needed to provide you with a little more… value? The makemv command adds that value.
Keep reading to learn exactly what the makemv command is, its benefits, and how to use it to bring more value to your searches.
What is the makemv command in Splunk?
Makemv is a Splunk search command that splits a single field into a multivalue field. This command is useful when a single field has multiple pieces of data within it that can be better analyzed separately.
An example of a situation where you’d want to use the makemv command is when analyzing email recipients. “Recipient” is a single field that holds multiple values, but if you want to find a single value, it would require a lot of resources (and time) to search for it. Instead, you can use makemv to display multiple values of a single field as its own field.
Benefits of the makemv Command in Splunk
- Analyze multiple values within a single field
- Speed up your searches
- You don’t have to create a new field to see the multiple values
- You’re able to search using the search head without exhausting your search cores
How to Use the makemv Command
To demonstrate how to use the makemv command, we’re going to use the following scenario:
Three people on your team received an email. These people are: Elmer, Bugs, and Yosemite. However, the email they received wasn’t from your internal team. Instead, it was a phishing email that has the potential to jeopardize the entire company. You know that when Bugs received the email, he opened it, and you suspect that the bad actors took over his account to send more spam emails to the entire company. It’s critical that you as the Splunk administrator get ahead of this issue immediately. To get started on your investigation, you need to find not only the email that was sent to these three individuals, but you need to find the emails that were sent directly to Bugs.
Let’s use the makemv command to solve this problem in this scenario.
Step 1: Start your search.
Use the search string below to start your initial search. Here, we’re telling Splunk to return to us all the recipients of the phishing email.
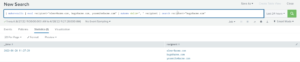
| makeresults | eval recipients=”elmer@acme.com, bugs@acme.com, yosemite@acme.com”
Step 2: Use the makemv command along with the delim argument to separate the values in the recipients field.
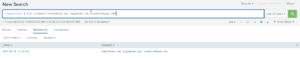
 Now that we have all the recipients of the email, we’re ready to look at the individual recipients as part of our investigation. Along with using the makemv command to find our specific recipient, Bugs, we’re using the delim argument to separate the email addresses into their own lines within the field. This makes the data easier to work with and puts it in the traditional makemv format in our table. The delimiter here is a comma since our email data is separated by commas.
Now that we have all the recipients of the email, we’re ready to look at the individual recipients as part of our investigation. Along with using the makemv command to find our specific recipient, Bugs, we’re using the delim argument to separate the email addresses into their own lines within the field. This makes the data easier to work with and puts it in the traditional makemv format in our table. The delimiter here is a comma since our email data is separated by commas.
| makeresults | eval recipients=”elmer@acme.com, bugs@acme.com, yosimite@acme.com” | makemv delim=”,” recipient
Step 3: Find the emails where Bugs is a recipient.
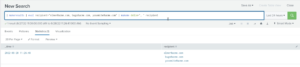
The great part about the makemv command is that you can find the emails where Bugs is a recipient rather than finding all the emails sent to the company and sorting for Bugs that way. This step in the makemv process is what makes it so efficient and valuable to have in your Splunk search repertoire.
| makeresults | eval recipients=”elmer@acme.com, bugs@acme.com, yosimite@acme.com” | makemv delim=”,” recipient | search recipient=”bugs@acme.com”
Extract field values with regex
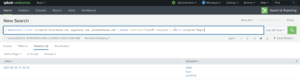
The makemv command can also use the regex command to extract the field values. In this example, we’re using the regular expression or “tokenizer” to match the string against the word characters in the email address.
| makeresults | eval recipients=”elmer@acme.com, bugs@acme.com, yosimite@acme.com” | makemv tokenizer=”(/we+)0” recipient | search recipient=”bugs”
 split Command vs. makemv Command
split Command vs. makemv Command
The split command in Java or Python and the makemv command in Splunk are similar in that they both separate values by a delimiter, but the primary difference is that the split function only separates the data into separate strings, it does not separate it into separate fields. When searching for data in Splunk, speed and ease are the name of the game, so makemv is the better choice between the two in this scenario.
Now that you have some basic understanding of the makemv command, try it out in your environment. Happy Splunking!
Splunk Pro Tip: There’s a super simple way to run searches simply—even with limited knowledge of SPL— using Search Library in the Atlas app on Splunkbase. You’ll get access to thousands of pre-configured Splunk searches developed by Splunk Experts across the globe. Simply find a search string that matches what you’re looking for, copy it, and use right in your own Splunk environment. Try speeding up your makemv search right now using these SPL templates, completely free.
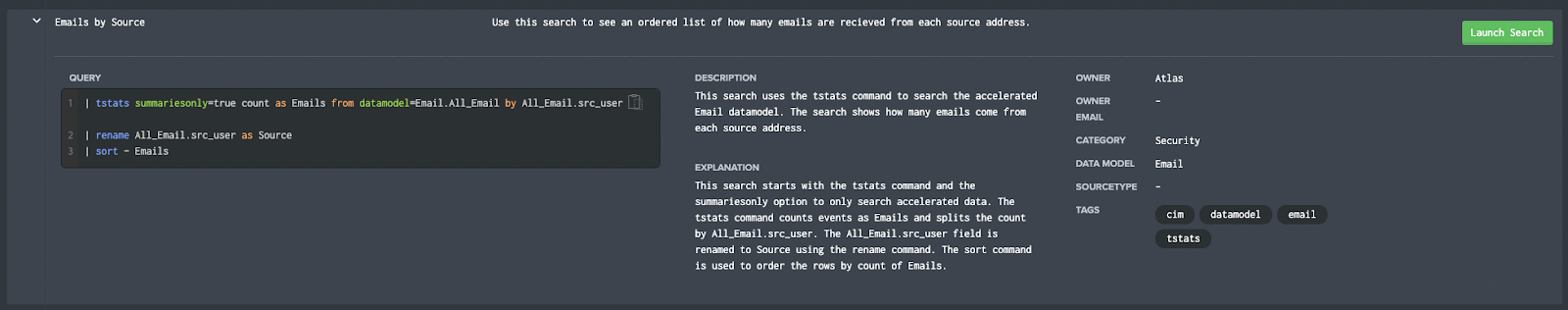
Run a pre-Configured Search for Free
If you found this helpful…
You don’t have to master Splunk by yourself in order to get the most value out of it. Small, day-to-day optimizations of your environment can make all the difference in how you understand and use the data in your Splunk environment to manage all the work on your plate.
Cue Atlas Assessment 30-day free trial: a customized report to show you where your Splunk environment is excelling and opportunities for improvement. You’ll get your report in just 30 minutes.