What are the basics of Splunk search?
The basics of Splunk search include the Splunk Web Interface, search controls, timeline and events, search commands, and data visualizations. Together, these elements make up the building blocks of all SPL search strings to view, analyze, and manipulate the data in your Splunk environment.
Splunk Web Interface
Simply put, the Splunk Web Interface is Splunk’s UI (user interface). It’s where you’ll perform searches, use search commands, and visualize data. To begin the basics of search in Splunk, you’ll need to get your data into the Splunk Web Interface.
Search Controls
Search controls in Splunk are responsible for helping you navigate the Splunk Web Interface as you conduct your searches. There are several functions available within the search controls, including:
- The Splunk Logo: Go back to your Splunk home screen.
- App: Search & Reporting: Manage and download other Splunk apps from Splunkbase.
- Administrator (username): Personalize your settings in Splunk.
- Messages: View health notifications and other pertinent messages from Splunk.
- Settings: Customize your Splunk features.
- Activity: View triggered alerts.
- Help: Discover Splunk resources and learning material.
- Find (Search): Search for items or keywords in your Splunk environment.
Timeline and Events
There are two additional elements alongside the search controls in Splunk: the timeline and events tab. The timeline provides a visual representation of the events that are taking place in your Splunk environment over time. Timeline and events are especially useful to identify patterns within your Splunk data so that your team can act quickly when activity that is outside the norm occurs.
Now that we’ve covered the basics of Splunk search, let’s go over how to create a Splunk search from scratch.
How to Create a Splunk Search
Splunk searches use SPL commands and arguments to retrieve, organize, and display data. A pipe character is used to start each new search string, followed by the command. Here’s the format for creating a Splunk search:
- Choose an index and a time range.
- Include filters to narrow down your search to only the data you want to see.
- Add commands and arguments one by one using the pipe character.
- Include the table, chart, or other visualization after all of your search strings are included.
- Save your search as a report, dashboard, or alert.
Splunk Pro Tip: There’s a super simple way to run searches simply—even with limited knowledge of SPL— using Search Library in the Atlas app on Splunkbase. You’ll get access to thousands of pre-configured Splunk searches developed by Splunk Experts across the globe. Simply find a search string that matches what you’re looking for, copy it, and use right in your own Splunk environment. Try speeding up your search right now using these SPL templates, completely free.
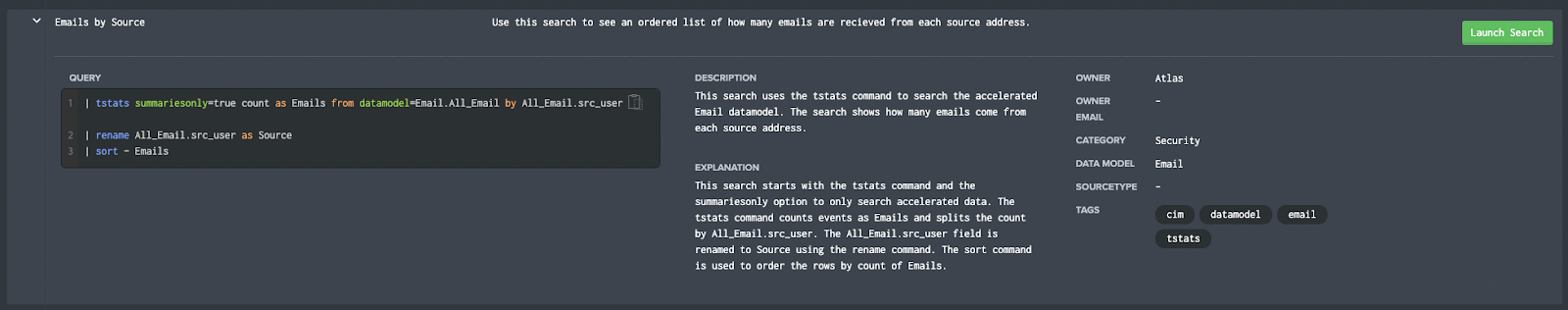
Run a pre-Configured Search for Free
Basic Search Commands in Splunk
There are several search commands in Splunk that you can use to add further context to your data. Three of the most common elements you’ll use in nearly every search you run are index, time-range selection, and search filters. While these aren’t technically commands, they do help your commands work better, so we included them in this section.
- Index: Specifying an index is step one of any basic or complex search because it tells Splunk where to look up the data. There are virtually no use cases where you won’t need to specify an index for your search, so you should always specify an index, here’s why.
- Time-range selection: Choosing a time-range makes your search faster and more efficient. Selecting too small of a time-range can limit the data that returns from your search, but too large of a time-range can be wasteful of your Splunk resources and take much longer than necessary. If you’re not sure exactly what time-range to start with, do not choose real-time or all time.
- Search Filters: Similar to index and time-range selection, search filters help you further sort your data to retrieve only the most relevant information to your search. Using search filters also results in more efficient searches.
Eval Command: The eval command is incredibly robust and one of the most commonly used commands that calculates an expression and applies that value to a brand new destination field.
Stats Command: The stats command calculates statistics. By using the stats command, you can find a high-level calculation of what’s happening to your machines.
Rex Command: When extracting fields, you can use rex commands to manipulate, calculate, or display specific data by itself.
Dedup Command: When you have events that include the same values in certain fields, you can use the dedup command to remove them.
Where Command: Another way to filter search results is the where command which uses true or false expressions to return search results.
Rename: This formatting command is used to rename a field. The syntax is <fieldname><newfieldname>
Head/Tail: By default, the head command returns the last 10 results of a search in descending order. The tail command does the same thing, only it starts at the end of the result set.
Top/Rare: The top command allows you to easily find the most common values in fields while the rare command returns the least common values in fields. These commands will also help you find information behind your event values like count and percentage of the frequency.
Sort/Reverse: The sort command is responsible for sorting search output data by field. The reverse command reverses a set of events.
Subsearches: A subsearch returns data that a primary search requires. The subsearch always runs before the primary search. It uses square brackets [ ] and an event-generating command.
Join Command: To combine a primary search and a subsearch, you can use the join command. All you need to use this command is one or more of the exact same fields between both searches.
Transaction Command: To find, group, break up, or display raw data for similar events, use the transaction command.
Inputlookup Command and Outputlookup Command: These commands are used to save and retrieve searches you’ve made in a lookup table.
Visualizing Data and Splunk Search Results
We’ve created our search and formatted it. Now it’s time to visualize the data in a way that makes it easy to digest for yourself and any stakeholders who’ll need to view it. To do that, we use a variety of data visualizations in Splunk.
- Table/Fields: The table and fields commands in Splunk allow you to retrieve specific fields within your data without conducting a search for all the fields in the data. The table command, specifically, pulls the data into a tabular format.
- Chart/Timechart: The chart command is a transforming search command that allows you to put your data into a graphical visualization. The timechart command formats the results into an x and y chart where time is the x -axis and the y -axis is a specified field.
Splunk Search Basics
Searching in Splunk is quite straightforward when you have all the options at your fingertips. That’s why we created this guide. Bookmark this article for future reference as you become familiar with each search command. Practice using them and soon enough, you’ll be a Splunk search pro!
If you found this helpful…
You don’t have to master Splunk by yourself in order to get the most value out of it. Small, day-to-day optimizations of your environment can make all the difference in how you understand and use the data in your Splunk environment to manage all the work on your plate.
Cue Atlas Assessment: a customized report to show you where your Splunk environment is excelling and opportunities for improvement. Once you download the app, you’ll get your report in just 30 minutes.





