What is the table Command?
Splunk’s table command is essential for formatting results on dashboards and in searches. Using the table command enables Splunk users to limit and order the results of a search in their SPL. Table is useful when you want to see your search results in a tabular format and include only the fields that are important to you. To use table, insert the command like any other Splunk command into your SPL, then include the fields in the specific order you want them listed in the table output. Columns are displayed in the order specified in the SPL and each row represents an event. Visualizing your search results in a tabular format makes it very easy to isolate the fields you care about and can be used to quickly create dashboard visualizations.
Basic command syntax
index=win*
| table index host OpCode
In this search, 3 fields (index, host, OpCode) are extracted from all indexes that begin with ‘win’ displayed in table form. The resulting command will appear in a table format shown below:
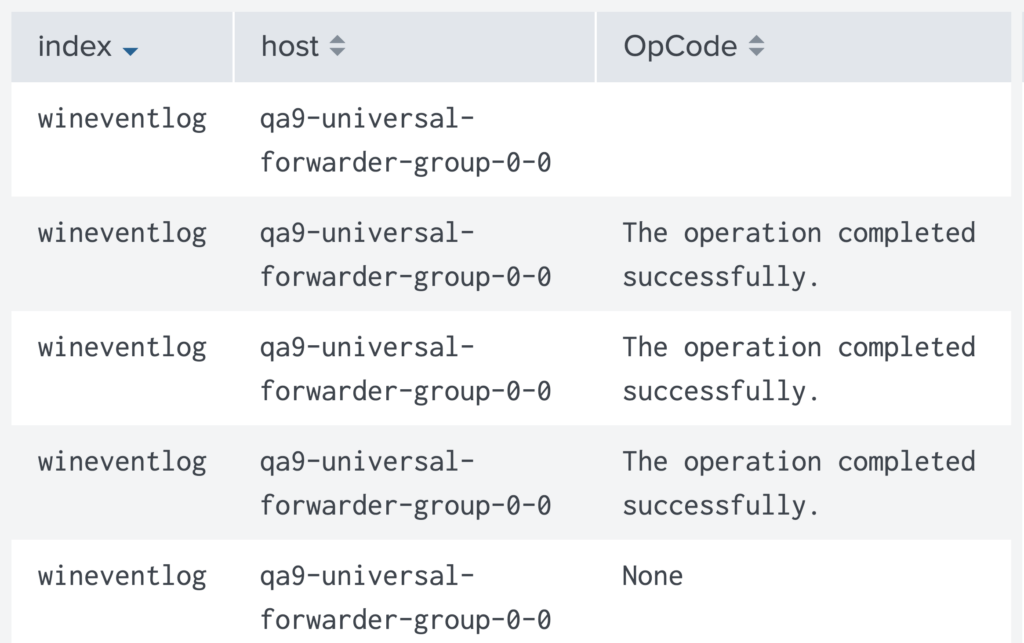
It’s important to understand that the table command does not filter results that lack values in the selected fields. As shown above, the second row does not have an OpCode value in the event, but it is still present in the data. Use the search or where command to perform the additional filtering if you would like to remove those events.
How Does the table Command Affect SPL Logic?
Another important concept to understand about table is that it impacts the SPL logic of the search. Any fields not explicitly included in the table fields will ‘drop off’ and cannot be referenced following the table command in the SPL. In the example below, the field ‘test’ will not be available for reference after the table command because it is not referenced in the table fields.
index=win*
| eval test="Test Data"
| table index host OpCode
SPL that handles large amounts of data can be slowed by unnecessary fields increasing search computation. Using table can reduce unnecessary data in your search results, but the fields command is generally better practice because it helps to keep or remove fields from search results based on the field list criteria.
Utilizing '*' Wildcards
Finally, table can utilize wildcards ‘*’. Wildcards match on any or no characters. This can be beneficial when dealing with fields that have similar prefixes or suffixes. The following example would table any fields starting with “in” in alphabetical order. You can also use multiple wildcards in one statement (such as ‘in*e*’) which would capture anything that starts with ‘in’ and is followed by an ‘e’ (for example “index” and “interloper” would be captured when the ‘in*e*’ is evaluted.
index=win*
| eval test="Test Data"
| table in*
Wildcards are useful with the table command for debugging searches, as they can display what the values of fields are in a tabular format, which makes it easier to see which fields are currently being captured by a search. A really useful tip is to use the “| table *” command to see all fields that are currently in your search results without having to know which fields you want in your table.
index=win*
| table *
Conclusion
The table command in Splunk is a powerful tool that can be used to help your searches in the following ways:
- Enhanced Readability: The command is used to display search results in a table format, focusing on specific fields making data easier to analyze.
- Selective Field Display: It allows customization of search output by letting users select which fields to display in the table, enabling focused data visualization.
- Customization and Flexibility: The command offers flexibility in data presentation, allowing users tailor the output to specific analytical or reporting needs.





