In our daily use of computers for home and business, we are consistently faced with the task of logging into our systems, applications, and websites, which can be a hassle as it forces us to try to memorize countless passwords. System administrators can ease this burden for their users by implementing a single sign-on solution.
What is SSO?
Single sign-on, or SSO, is the automatic transference of login credentials to provide seamless and instant access to multiple systems, apps, or websites. Implementing SSO in your environment can provide many benefits and reduce the hassles associated with accessing your IT systems.
Benefits of SSO Implementation
Implementing Single Sign-On (SSO) in your environment can provide numerous benefits. With SSO, users can provide their credentials once to their host system for login, and every app can then utilize the host credential for immediate access. This eliminates the need for a password vault app to track passwords, making it easier for users to access multiple systems and applications.
As a desk-help technician, you may be responsible for assisting your users to access systems and applications. SSO can reduce the number of help-desk tickets for account lockouts and password resets, saving time and effort.
As a system administrator, you are responsible for securing your network and systems. SSO can increase the security posture of your environment by preventing brute-force attacks from hackers.
Cloud-based solutions heavily utilizing SSO allow quick and easy access to web-based systems and applications. Consider implementing SSO to streamline access and improve security in your organization.
Types of Single Sign-on (SSO)
Security Assertion Markup Language (SAML): This is a single sign-on solution for web applications. The web application that you (the end user) are attempting to access is called the service provider in SAML. The system that certifies who you are is called the identity provider. It uses tokens and assertions to pass information about an end user to an identity provider. The identity provider then checks your credentials and informs the service provider whether to allow or disallow access.
Federated Single Sign-on: This solution is used in Cloud and Web identity service accounts. It allows seamless access to applications from a different service provider. For instance, you can authenticate into a Google web app, and if Google had a security trust relation with LinkedIn, you could automatically access the LinkedIn website without re-enter credentials.
CAC Authentication: This a type of single sign-on technology that provides SSO capabilities to applications using a smart card called Common Access Card or CAC. CACs are widely used in military and government computing environments for access to networks and systems.
Splunk’s web consoles can be configured to use SSO technologies such as SAML and also have built-in CAC authentication capabilities.
Implement Splunk Built in CAC Authentication
If your organization has Splunk and uses smart cards for accessing computer systems, you may want to explore Splunk’s built-in Common Access Card (CAC) authentication capability.
Splunk’s CAC authentication has several requirements, including using LDAP for user authentication, requiring the use of HTTPS for Splunk Web access, and using Mutual TLS (mTLS). When using mTLS, clients are required to present a valid certificate when they authenticate. In this case, the client certificate resides on the smart card utilized to access Splunk Web.
You can configure LDAP in Splunk using the authentication.conf file, or in Splunk Web by clicking Settings > Authentication methods and selecting ‘LDAP’ from the authentication method list. You will need to work with your Active Directory administrator to obtain the required field values for this form.
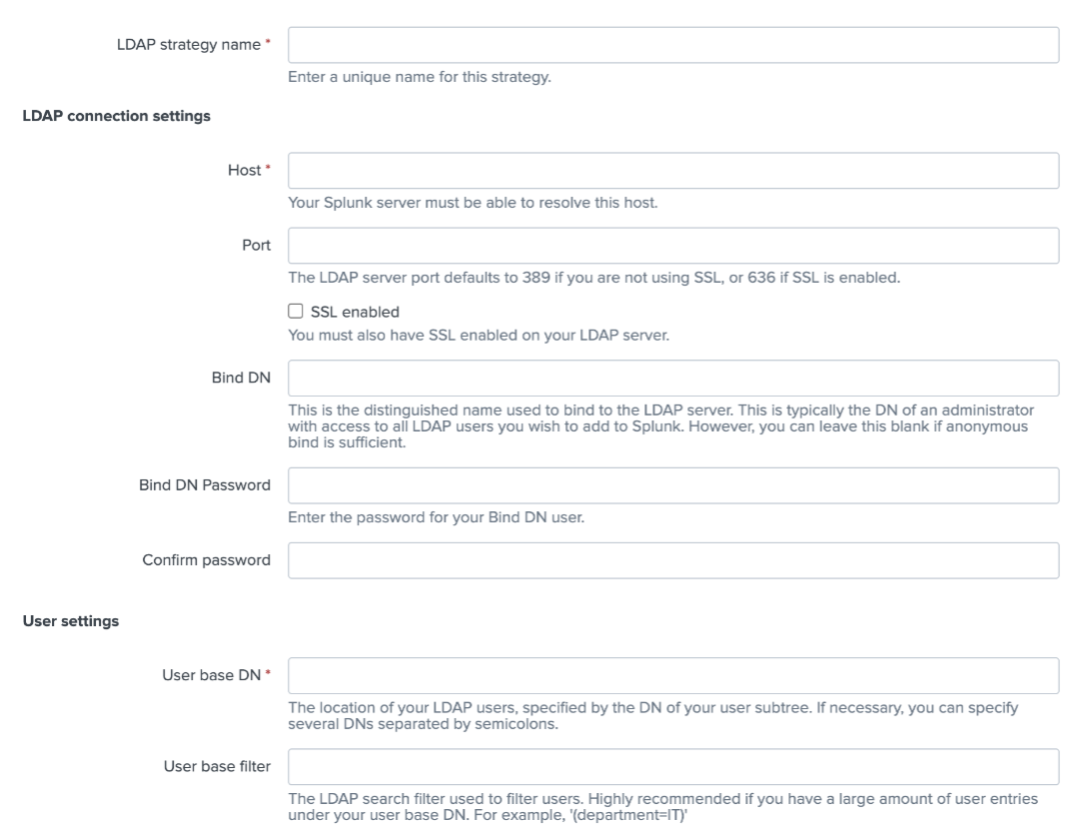
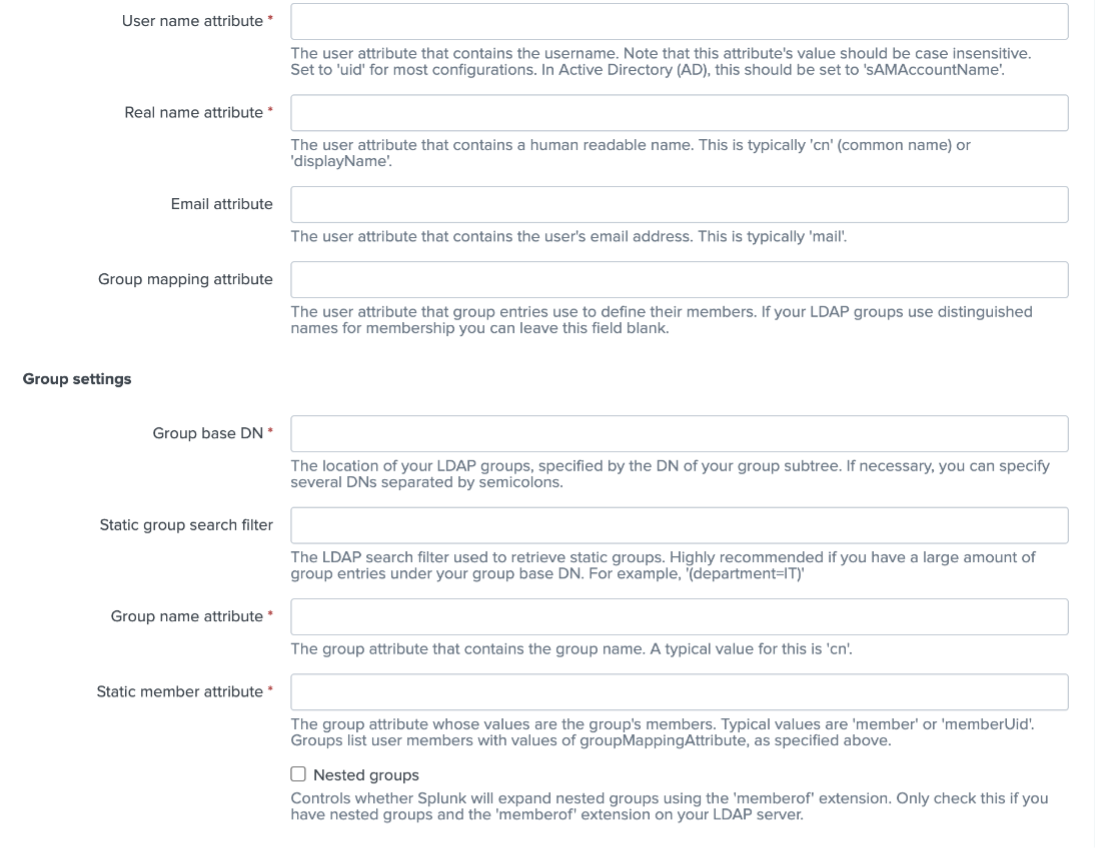
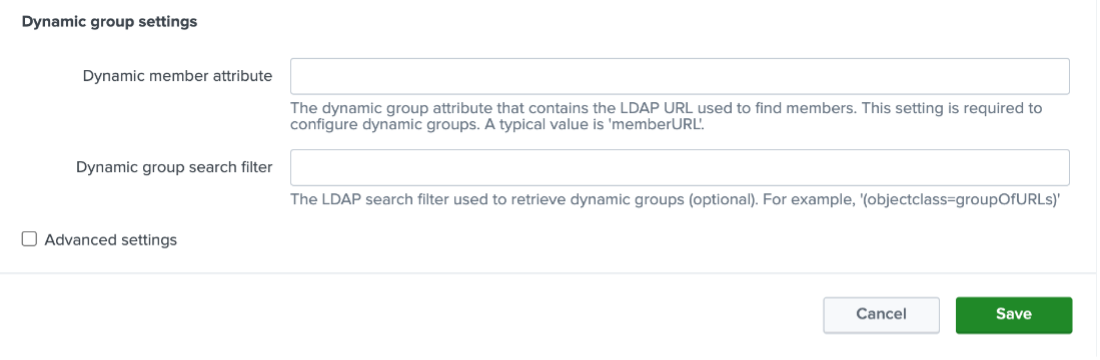
This will configure Active Directory with a role domain so that it can function as the credential provider.
You will then need to map Splunk roles to the appropriate AD security groups for establishing role-based access levels of admin, power, user, or any custom role that is configured. You can map AD groups to Splunk roles in authorize.conf, or by using Splunk Web. For instance, in the example below, we see that the Splunk-Admin LDAP group is assigned to the Splunk ‘admin’ role:
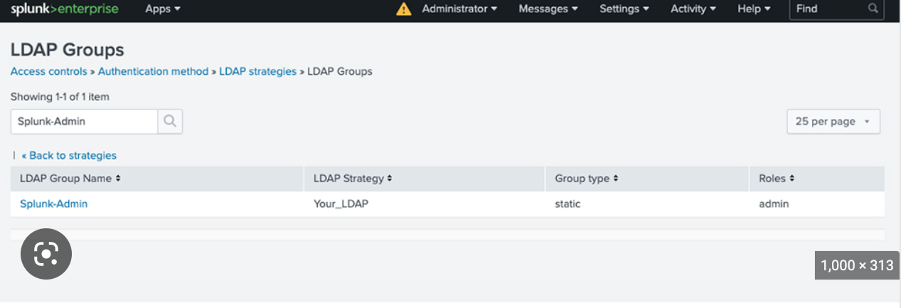
User accounts in an Active Directory domain can be configured with security groups based on the required level of access.
Splunk requires special configuration for using TLS communications between the client and Splunk Web console. This requires the use of third-party certificate authority signed certificates and specific settings in the web.conf configuration file:
web.conf
[settings]
enableSplunkWebSSL = true
privKeyPath = /opt/splunk/etc/auth/mycerts/mySplunkWebPrivateKey.key
serverCert = /opt/splunk/etc/auth/mycerts/mySplunkWebCertificate.pem
Splunk also requires configuration for using mTLS communications and enabling card-based authentication. The settings for this are applied in the server.conf and web.conf configuration files.
server.conf
[SSLConfig]
SSLRootCAPath = <location of the root CA certificate for HTTPS connections to the instance>
trustedIP = 127.0.0.1
web.conf
[settings]
requireClientCert = true
sslRootCAPath = <location of the root CA certificate to authenticate web clients connecting to Splunk Web, overrides the setting in server.conf>
enableCertBasedUserAuth = true
SSOMode = permissive
trustedIP = 127.0.0.1
certBasedUserAuthMethod = <string>
certBasedUserAuthPivOidList = <string>
After re-starting the Splunk instance, you can test your CAC authentication by clearing your browser cache and launching a Splunk Web page. If there are any problems with the configuration, revisit the configuration settings, validate your user account settings on the domain, and try again.
Conclusion
Single sign-on is a valuable feature for helping your users manage access to applications. It reduces password reset and unlocked account requests while providing better access security for your applications. Common Access Card (CAC) authentication supports the use of government agency smart cards to gain access to buildings, controlled spaces, computer systems, and networks, as well as Splunk Web. To ensure a secure and efficient implementation, it is essential to follow the proper configuration steps as well as test your CAC authentication after configuring your system.
If you found this helpful…
You don’t have to master Splunk by yourself in order to get the most value out of it. Small, day-to-day optimizations of your environment can make all the difference in how you understand and use the data in your Splunk environment to manage all the work on your plate.
Cue Atlas Assessment: Instantly see where your Splunk environment is excelling and opportunities for improvement. From download to results, the whole process takes less than 30 minutes using the button below:





