Beginner and veteran Splunkers have felt this before: running a search hoping to get valuable information only to sit and wait for what seems like forever for it to run. There are many ways to combat slow searches using Splunk search modes. They can help return results faster or make results more comprehensive which avoids you having to re-search data.
This blog post is here to fill you in on the pros and cons of all three Splunk search modes: fast mode, smart mode, verbose mode.
What are Splunk search modes?
Splunk search modes help you find the data you need by prioritizing different elements of a search. The goal of using search modes is to get results quickly or achieve a comprehensive search output.
There are three different search modes, each with its own benefits and drawbacks.
The three Splunk search modes are: Fast, Smart, and Verbose.
Fast mode: Prioritizes speed over the completeness of results.
Smart mode: The default mode of searching in Splunk. Gives you the best of both worlds, prioritizing speed or completeness depending on your search.
Verbose mode: Prioritizes completeness over speed; returns all fields and event data.
Fast Mode
Fast mode is, as the name implies, the quickest search mode in Splunk. Fast mode prioritizes speed over completeness of data by disabling field discovery, meaning the search only returns the default fields (host, source, sourcetype, _time) unless a specific field is searched upon, at that point Splunk will only extract whatever field(s) was specified. This allows the search to run much faster but can be very limited by what fields you already know can be extracted. If, for example, you don’t know that source ip is a field that is able to be extracted in your data then using fast mode will not highlight that.
If you know which fields your search needs and you want it to run as quickly as possible, fast mode will work for you.
Smart Mode
Smart mode is a combination of both fast mode and verbose mode and will return the results that work best for your search. If you are running an event search (a search without a transforming command) all the fields that can be extracted will be. This allows you to see what fields can be searched with to help create the best search you can to complete your needs. If you are running a search with a transforming command, like a stats command for example, smart mode will only extract the fields that you specify, much like fast mode.
This is the default search mode in Splunk, and for most Splunk users it will be the only search mode they need.
Verbose Mode
Verbose mode is the slowest of the 3 Splunk search modes as it discovers and extracts all of the available fields even if a transforming search is run. This means if you run a stats count by host search you are still able to click back to the Events tab to see the individual events and the fields extracted. This can be helpful if you want to refine your search by being able to flip back and forth between the events and statistics tabs without having to rerun or comment out parts of your search.
This comes at the cost of performance which takes a big hit from having to discover and extract all fields no matter what search is run.
How to use Splunk search modes
Thankfully Splunk has made using search modes as easy as clicking a single button. Whenever a search is run below the search window there will be a box that shows the current mode you are searching in. Clicking this box creates a drop down with fast mode, smart mode, and verbose mode as options with a brief description of each. Clicking on any of these modes will rerun your search in the mode you have chosen. From there you can continue to work on your search as desired with the ability to change modes again at any time.
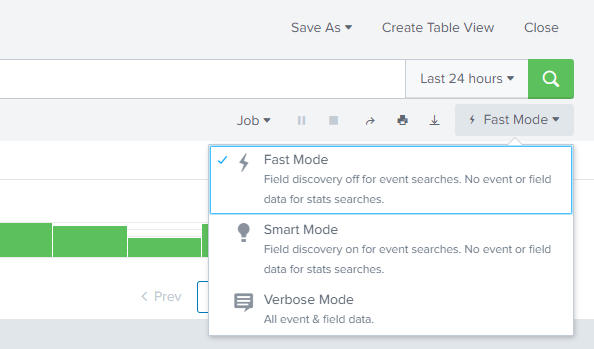
Use Cases
Let’s say you are a Splunk admin tasked with figuring out the count of Windows EventIds in your data. Being familiar with Splunk and windows event logs you already know that EventID is a field that can be extracted in Splunk. You want your search to run quickly and efficiently and don’t need any excess data. Therefore, you can choose to use either fast mode or smart mode. Due to the stats search in your command it is a transforming command so using smart mode with this search would perform the same as using fast mode.
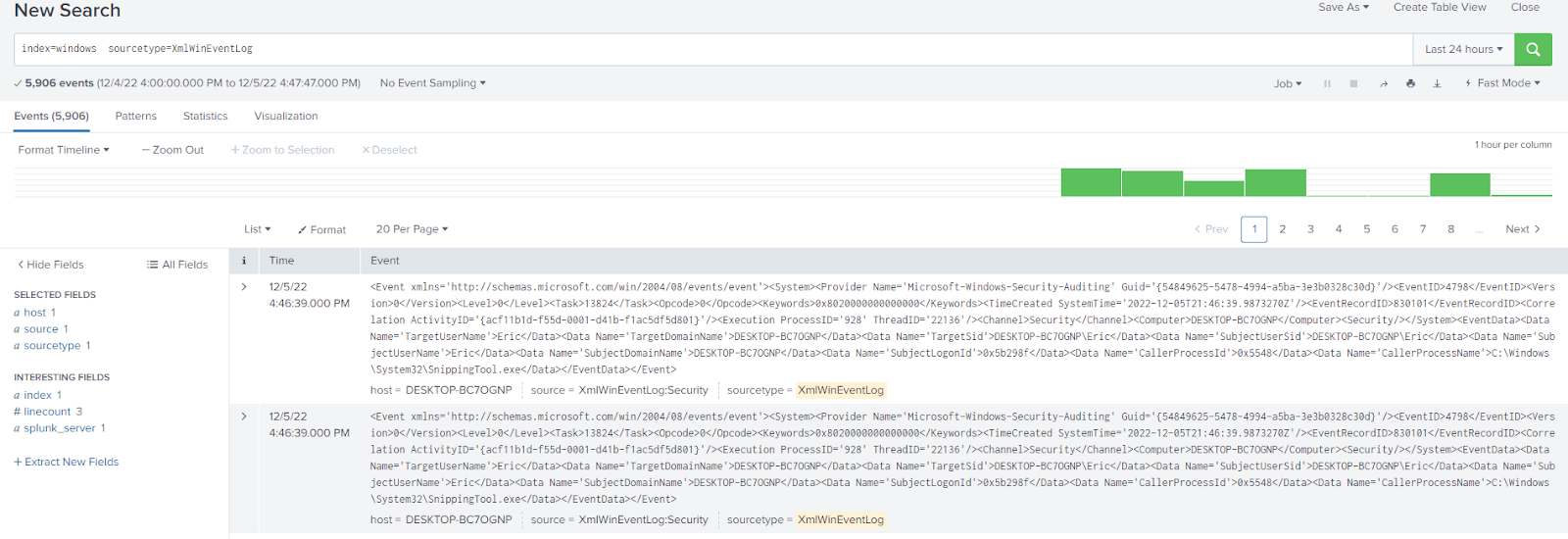
Using fast mode without a transforming command you can see only default fields are extracted:
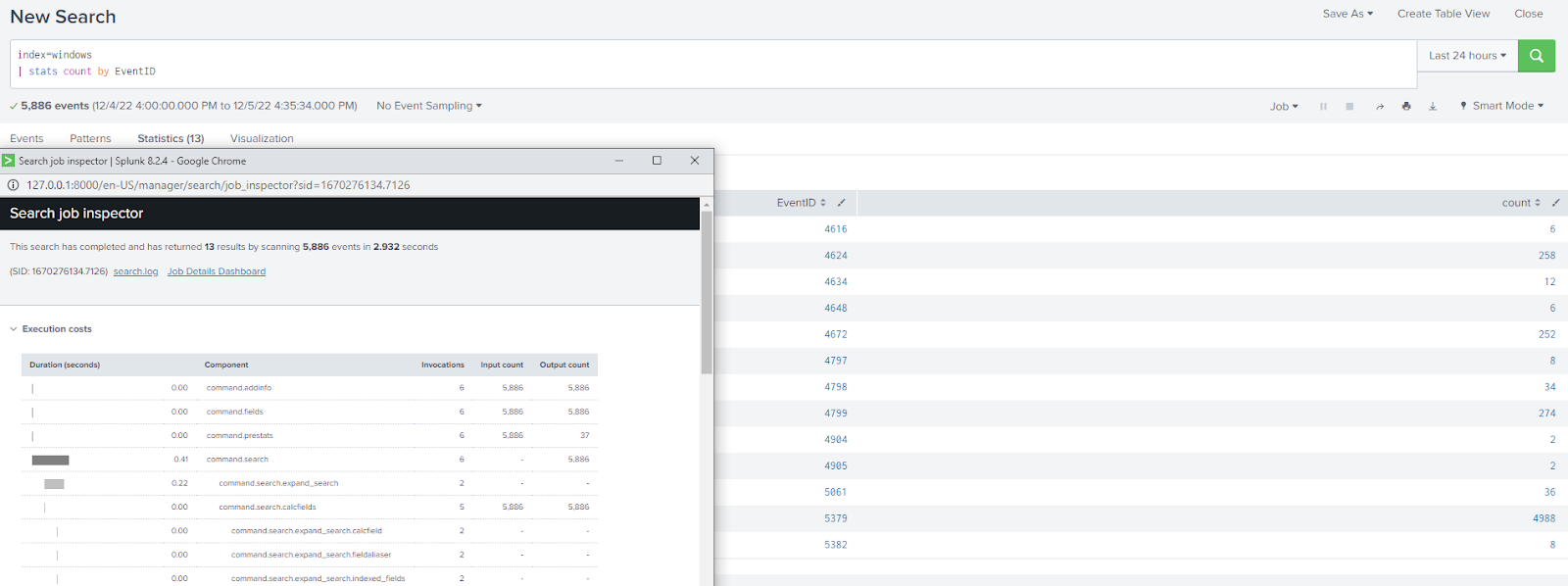
Using fast mode with a transforming command:
Using smart mode:
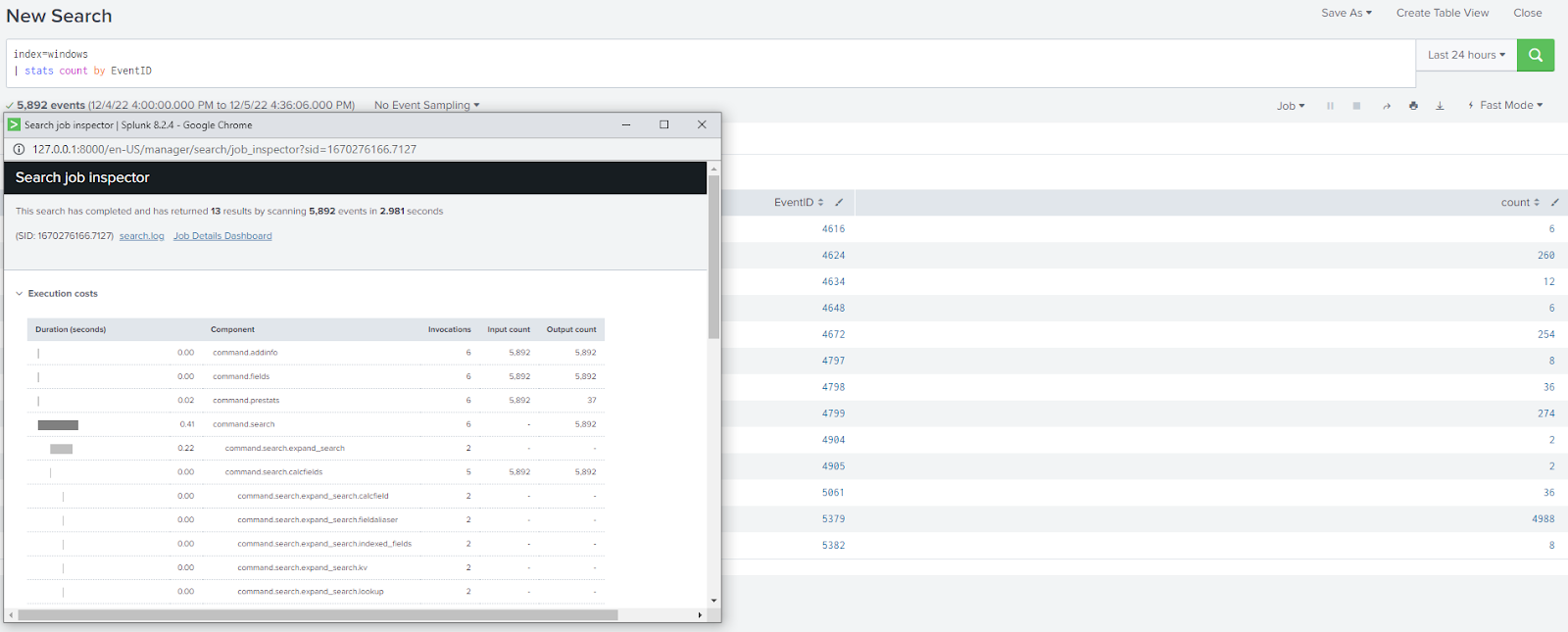
By choosing either of the modes you know you are getting the best performance for your search without having to worry about fields being discovered and extracted that you do not care about for the context of the particular search.
On the other hand, let’s say you are a Splunk user who is unfamiliar with windows event logs within Splunk. You know a count of EventIds would be useful but you would also like to be able to look at other fields that are extracted to fully craft your search to be exactly what you want to see. There are two ways to do this: smart mode and verbose mode. With smart mode when performing an event search all possible fields are discovered and extracted.

However, if you add in a transforming search but want to look at the events again to see if there may be additional fields that could add valuable context to your search you are unable in smart mode as now smart mode is acting as if it was fast mode and only extracting the fields specified in the search.
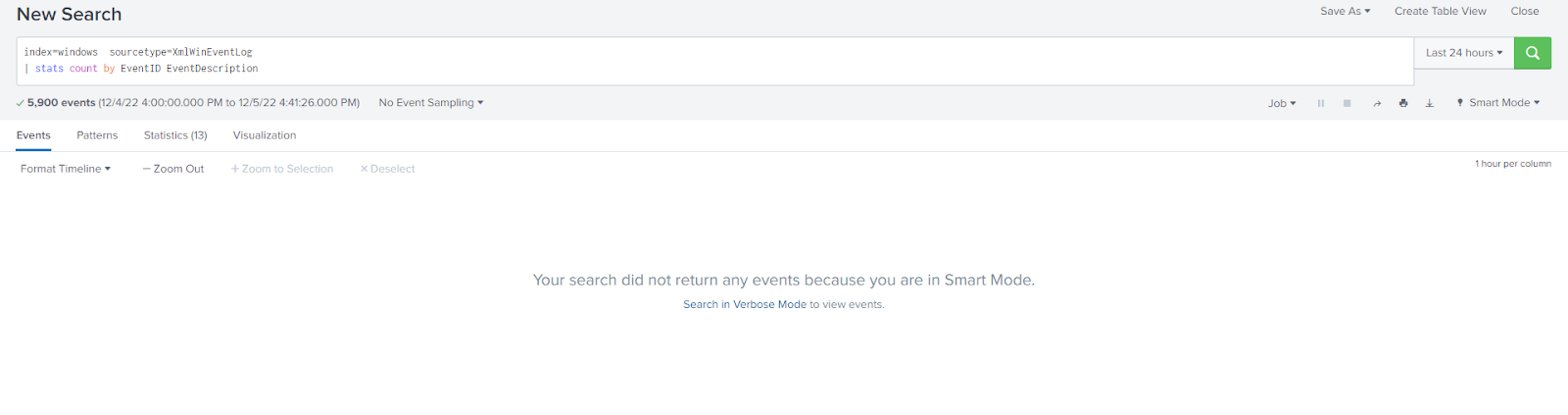
You can remedy this by running the search in verbose mode. By running in verbose mode, the stats command performs the statistical transformation but the events and field extractions are also performed so you can switch between both the Events tab and the Statistics tab and both will be populated.
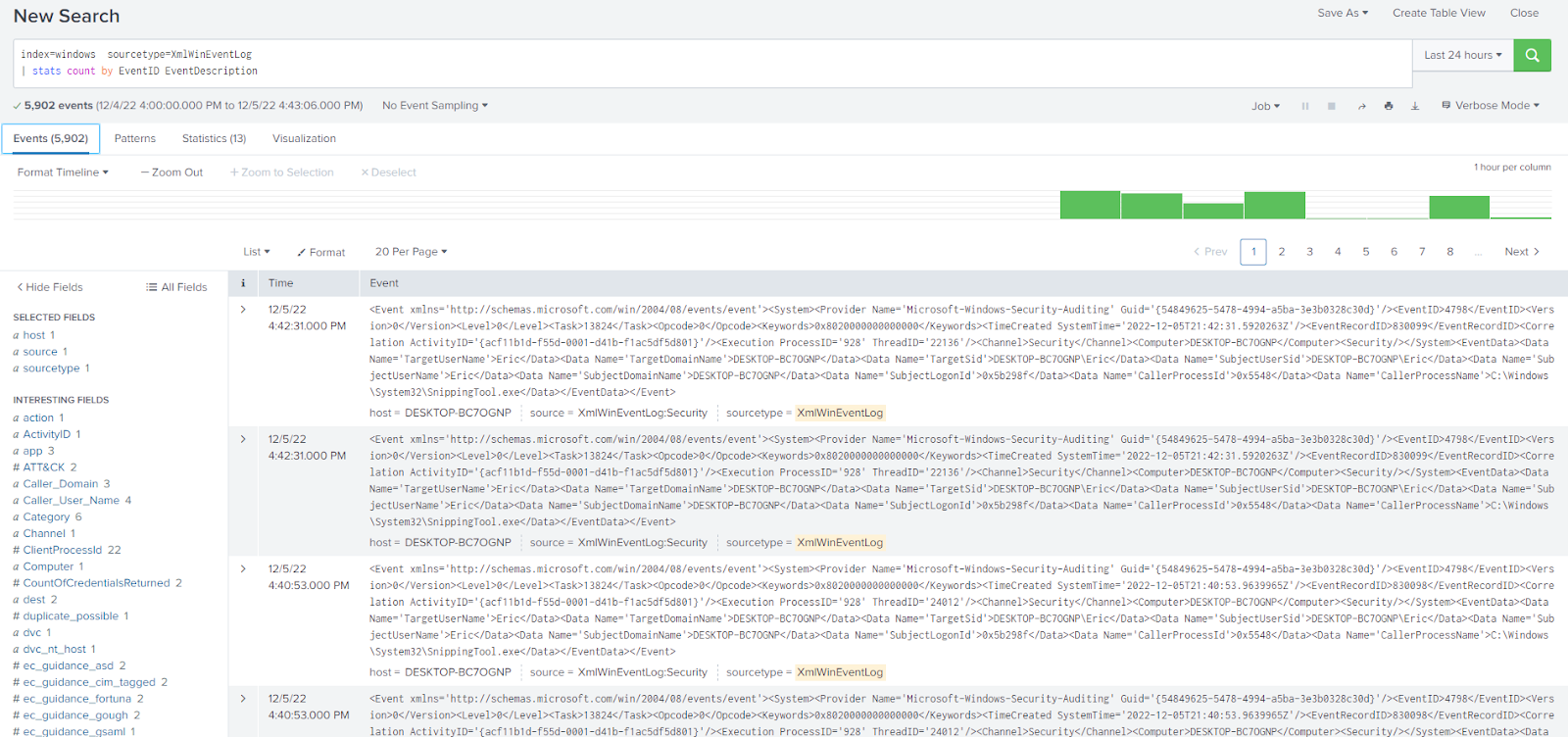
This will allow you to look at the events and see what other fields may be useful to your search without having to remove or comment out the transforming section of the search. This will come with a performance hit, however, so in large environments, it may not be advisable to leave verbose mode on at all times.
Improve Your Searches with Search Modes
With Splunk choosing between the search modes is very easy but can be a very powerful tool to increase search performance. Fast mode offers high-speed searching with less data extraction, verbose mode offers slower searching but with maximum data extracted, and smart mode, the default search mode, offers a great blend of both depending on your search. It is very easy to play around with the different modes to see which offers the best performance for your needs, it’s as simple as clicking one button under the search bar. With this new tool under your belt, you are more ready to face down that stubborn search you are working on and become more familiar than ever with Splunk.
You don’t have to master Splunk by yourself in order to get the most value out of it. Small, day-to-day optimizations of your environment can make all the difference in how you understand and use the data in your Splunk environment to manage all the work on your plate.
Cue Atlas Assessment: Instantly see where your Splunk environment is excelling and opportunities for improvement. From download to results, the whole process takes less than 30 minutes using the link below:




