Splunk’s Search Processing Language (SPL) offers powerful capabilities for data analysis and manipulation. Among its diverse commands, the selfjoin command stands out for its ability to join a dataset with itself. Let’s explore this command’s functionality, usage patterns, and practical applications.
Understanding the selfjoin Command
The selfjoin command enables users to combine a dataset with itself based on specified fields, creating relationships between events within the same dataset. This self-referential join is particularly useful when analyzing hierarchical relationships, finding patterns within the same data, or comparing events across different time periods. When the selfjoin command is executed, it matches events with the same field values within a dataset. So if you have the field ‘status’ with the value ‘failed’ across multiple events, those events will be groups if you specify ‘status’ with the selfjoin command. This is great for identifying relationships or clusters of related events.
Proper Syntax
The syntax for the selfjoin command follows this structure:
| selfjoin [overwrite=<bool>] [max=<int>] [keepsingle=<bool>] <field-list>
Parameters Explained:
- field-list – Specifies which fields should be joined. You can choose any number of fields to include, and it will join all matching values across the fields selected.
- keepsingle – Whether or not to keep the field values that have no other fields to match with are kept as part of the result.
- max – The maximum results which will be joined with the main results. By default, it is set to 0, which makes it have no limit. However, there is a hard-written maximum of 100,000 results.
- overwrite – Determines whether fields in the joined events should overwrite fields in the original event when they share the same field name.
For example, if you wanted to find back-to-back errors across different servers you can use a command like the following:
| selfjoin error
| stats count by server
This will join all values within the field “error”. When we count by the different server values, we are then going to see how many unique errors have been showing up by server.
Benefits of Using the selfjoin Command
- Pattern Detection – Enables the identification of event sequences within the same dataset. This makes it perfect for tracking user behavior or transaction chains. You can utilize it to understand workflow progressions and chase down correlations.
- Data Quality Management – Detect inconsistencies in records and validate integrity across events. Find data anomalies and duplicates through comparison.
- Business Intelligence – Reveal patterns of customer behavior and understand transaction relationships. Create service usage patterns and provide insights into process workflows.
Example Use Cases
Example #1: Detecting Multiple Failed Login Attempts
Use case: Identify potential security incidents by finding multiple failed login attempts from the same user.
index=network status=failed
| selfjoin user_id
| stats count by user_id
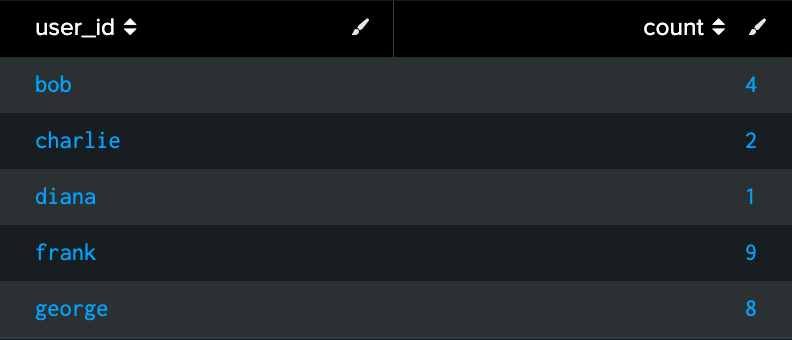
Description: The selfjoin command identifies multiple failed login attempts by matching events on ‘user_id’, ensuring that all failed login attempts from the same user are grouped together. After grouping, the ‘stats count by user_id’ command counts the number of failed login events per user, highlighting users who have encountered multiple failures. This query is particularly useful for detecting potential security threats such as brute force attacks, where an attacker repeatedly attempts to guess a user’s credentials. By analyzing the frequency of failed logins for each user, security teams can pinpoint suspicious activity and take preemptive action to secure accounts or investigate the root cause of login failures.
Example #2: Analyzing Transaction Patterns to Identify Potential Fraud
Use Case: Identify accounts with unusually large transactions compared to their previous patterns to detect potential fraud or spending anomalies.
index=bank_transactions
| selfjoin account_id
| where amount > 10000
| table account_id, transaction_id, amount
Description: The selfjoin command groups events with the same account_id, allowing comparisons between transactions within the same account. By using the where amount > amount condition, this query identifies accounts with transactions larger than any other transactions associated with the same account. The selfjoin command does not generate new fields but effectively reorganizes events for comparison. This analysis helps highlight accounts with spending spikes, aiding financial teams in identifying suspicious transactions or unusual patterns of behavior that warrant further investigation.
Example #3: Finding Service Failure Dependencies
Use Case: Identify service dependencies by analyzing logs to find services that frequently call each other, helping understand application architecture or detect unusual interactions.
index=service_logs
| selfjoin service_name
| table service_name called_service timestamp
Description: The selfjoin command groups log events with the same service_name, enabling the identification of services that interact repeatedly. By using fields like called_service and timestamp, the query highlights patterns where one service (service_name) frequently communicates with another (called_service). This analysis is especially useful for mapping service dependencies in microservices-based architectures, identifying critical service connections, or uncovering unusual service call patterns. The output can help engineers visualize the flow of requests and detect potential performance bottlenecks or misconfigured dependencies in the system.
Conclusion
The selfjoin command is a versatile tool in the SPL arsenal, offering powerful capabilities for analyzing relationships within datasets. By incorporating this command into your Splunk workflows, you can:
- Enhance Security Analysis: Recognize suspicious and unusual behaviors by users.
- Improve System Optimization: Identify resource usage patterns and gain insight on process workflows.
- Strengthen Data Monitoring: Ensure compliance with best practices of confidentiality and integrity.
Leverage the selfjoin command to uncover hidden patterns and relationships within your data, enabling deeper insights and more effective analysis.
To access more Splunk searches, check out Atlas Search Library, which is part of the Atlas Platform. Specifically, Atlas Search Library offers a curated list of optimized searches. These searches empower Splunk users without requiring SPL knowledge. Furthermore, you can create, customize, and maintain your own search library. By doing so, you ensure your users get the most from using Splunk.






