One of the most important elements of indexing and searching for logs in Splunk is properly dealing with timestamps.
Properly tracking time enables you to extract valuable insights from your data. This could mean identifying trends over time, spotting events that are out of pattern, or identifying when a number of events breaks an alert threshold over a given period.
Fortunately, Splunk has powerful functions like strftime and strptime that enable us to precisely query our data for the insights we want. In this post, we will demonstrate the value of these functions and provide examples of several real-world use cases.
What is the Splunk strftime Command?
Strftime is a Splunk search function that converts a UNIX time value to a human readable format. Splunk uses UNIX time for the contents of the _time field in events. This means that for any date or time-related calculations we want to perform in our searches, we can run the strftime function against the _time field in our data.
UNIX time is a common method for measuring date and time that measures the number of seconds that have elapsed since January 1, 1970. While this is a convenient method for computers to track time, it’s not very helpful for humans, which is why we need strftime.
What is the Splunk strptime Command?
Where strftime takes a UNIX time and converts it to human-readable format, strptime does the exact opposite. Strptime can take human-readable timestamps in your data and convert them to UNIX time. This is helpful when you have human-readable timestamps you need to re-format or use cases that require UNIX time while your data contains human-readable time.
The strftime vs. strptime Commands
Strftime and strptime are two sides of the same coin. Strftime stands for “String from time” and uses a UNIX timestamp to create a string showing a human-readable timestamp. Strptime stands for “String parsed time” and turns a human-readable timestamp into a UNIX timestamp. Together, these two functions unlock many use cases for our data.
The Benefits of strftime
Strftime enables precise handling of date & time information within your Splunk queries. There are two primary benefits to leveraging this capability which we will explore below.
Benefit #1 strftime supports other Splunk time functions:
While the input to the strftime function is often Splunk’s _time field, it doesn’t have to be. The strftime function can also use other Splunk functions as input, such as now() and time(). Because these functions return time in UNIX time format, we must use the strftime format to make this data human-readable. Failing to properly leverage strftime can cause a host of problems. Without it, any timestamps in UNIX time format will display that way in your search results. Additionally, the results of functions like now() and time() will not work in calculations that also include human-readable timestamps.
Benefit #2 strftime gives you segment-level control over your timestamps:
The strftime function takes two inputs: a timestamp in UNIX time format and a format specification. This means you can format your timestamps any way you want. Additionally, it means you can extract and reference individual segments of the timestamp, such as the month and day or the hour and minute. Because the format argument of strftime maps exactly to every element of a timestamp, using it ensures accuracy in all timestamp parsing. Parsing it any other way introduces the risk of inaccurate results.
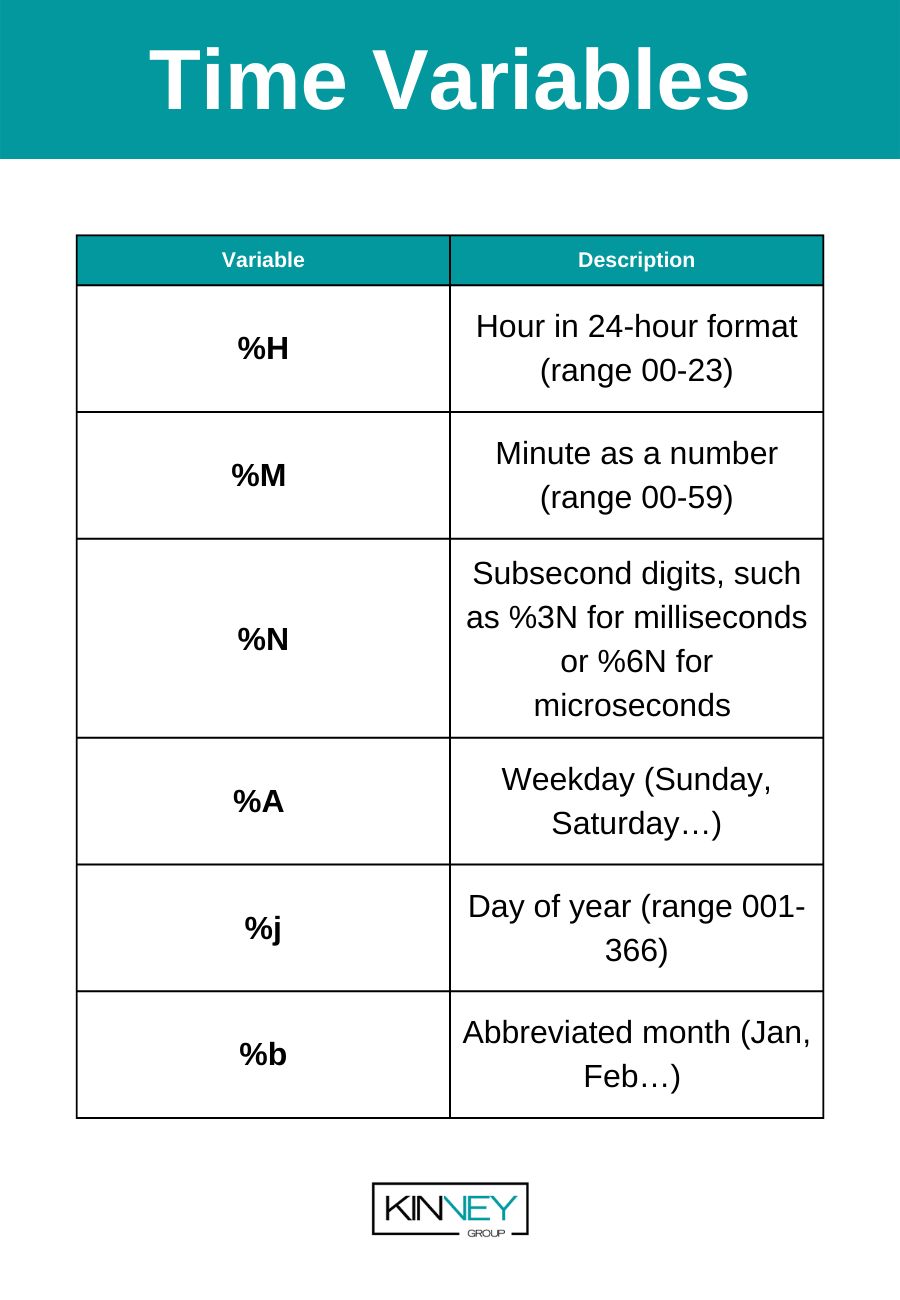
Splunk Time Variables
There are many different time variables available for use with strftime. A few examples are below:
Example strftime Queries
Below are some example queries that leverage strftime.
Example #1 Create a day of the week field:
When you have numeric data, such as timestamps, response times, or ages, binning allows you to group values into time intervals or age brackets. This simplifies the analysis by creating a clear structure. This query identifies the weekday of the event in question (such as Sunday or Saturday) and assigns it to a new field.
| eval weekday=strftime(_time, “%A”)
Example #2 Reference the current day of the month:
This query references the current time (i.e. search-time), identifies the day of the month, and assigns it to a new field.
| eval today=strftime(now(), “%d”)
Example #3 Create a timestamp relative to another timestamp:
This query references the event in question, creates a new timestamp at the top of the hour previous to that event, and then creates a human-readable version of the new timestamp using the format supplied.
| eval n=strftime(relative_time(_time, “-1h@h”), “%H:%M:%S”)
Splunk Pro Tip: There’s a super simple way to get visibility into the health of your universal forwarders using Forwarder Awareness in the Atlas app on Splunkbase. Here’s a snapshot of the data you’ll see with the click of a button. With this information, you’ll never have to wonder if all of your data is being ingested or whether it’s vulnerable. You can give it a go and decide for yourself right now, completely free. Try the Atlas Forwarder Awareness Tool Free in Splunkbase.
Use Cases for strftime Function
SCENARIO #1
Let’s say we’re using Splunk to monitor unauthorized system access. If an event is flagged for this reason, we can quickly and easily correlate that data to other data in a surrounding time period. Using the _time field of the event in question, we could create a new time window constraint on our query, such as:
| where _time > relative_time(now(), “-15m@m”)
We can then add that constraint to our fields list and make it human-readable by creating a new field:
| eval earliest=strftime(relative_time(now(), “-15m@m”), “&H:%M:%S”)
SCENARIO #2
In another scenario, perhaps we want to identify network traffic patterns throughout the workday. One way to do that would be to extract the hour field from our data like this:
| eval hour=strftime(_time, “%H”)
Then we can analyze our data at a more detailed level to see which hours throughout the day generate the most and least network traffic.
Conclusion
Strftime is a powerful Splunk command that enables accurate and easily repeatable reference to timestamps. It supports a wide variety of time variables in many different formats, so it is easy to customize for your specific needs. Additionally, because the _time field in Splunk data is stored in UNIX time, this command can be run easily against that field. Try some of the examples listed in this article on your own data, and you’ll quickly see the benefits of strftime.