When it comes to correlating information in searches to uncover unique patterns, there are several Splunk commands are commonly employed. For instance, you might opt for either a “Join” or “Append” to connect data sources before applying additional commands to analyze and isolate data for patterns. However, there is a command with similar functionality that also offers intriguing capabilities for pattern detection within data – the “map” command. In this article, we’ll delve into the use of the Splunk map command and provide insights into why it’s worth exploring in your Splunk search development.
What is Splunk 'Map' Command?
The Splunk map command provides the ability to loop on a search repeatedly for each input event or result. You can apply the map command to either an ad hoc or saved search. Similar to “Join,” it involves two searches, where the first search provides the input events that are utilized in the second search, which is looped upon to produce a result. However, caution is necessary when using the map command, as incorrect usage can pose security risks or result in potential data loss when run.
What Are The Benefits of Using Splunk 'Map' Command?
The Splunk map command permits the application of dynamically changing input values in a search, providing flexibility for pattern matching.
Furthermore, the Splunk map command is also similar in functionality to a “foreach” command, where all inputs are run against a search – a capability commonly employed in various programming languages.
The Splunk map command also provides a command argument known as “maxsearches” to restrict the maximum number of searches to run. When this argument isn’t set, the default number of searches executed is 10.
How to Use Splunk 'Map' Command?
To demonstrate the use of the map command, consider the following scenario: You have a data source containing company login information with the index name “system_logins.” When you execute the search “index=system_logins” in the Splunk Search and Reporting app, it yields the following output:
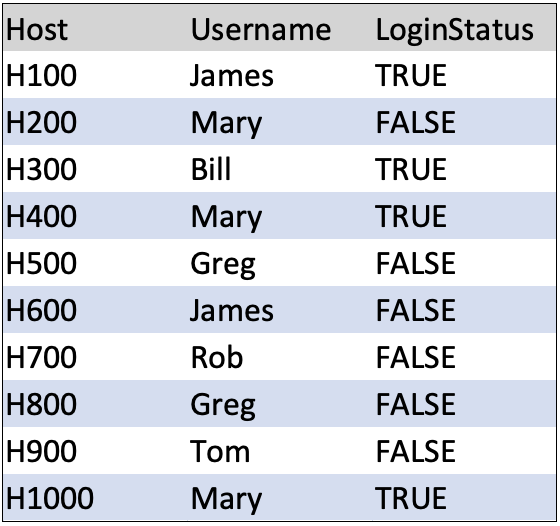
Additionally, you have another data source with human resource information indexed as “company_users.” Running the search “index=company_users” in the Splunk Search and Reporting app yields the following output:

You’ve been tasked with creating a correlation search using both data sources to determine the following information:
- Which users are currently logged into hosts?
- Which users are logged into more than one host?
Using the Splunk map command, this would be the final search:
index = company_users
| map search="index=system_logins Username=$User$ LoginStatus=TRUE"
Note that the “User” field from the “index=company_users” search will be fed into the map search as an input, which will be looped upon using the search in the map command search argument. The values from “User” that match the values found in the “Username” field in the “system_logins” index will yield the following result, answering the question of which users are currently logged into hosts:
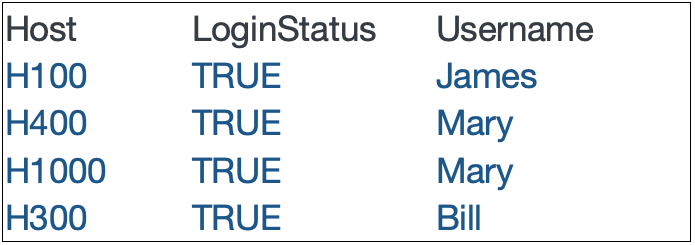
The next question can be answered by adding more logic to the search as follows:
index = company_users
| map search="index=system_logins Username=$User$ LoginStatus=TRUE
| stats dc(Host) as NumOfLogins by Username"
The search will now yield the following results, answering the question of which users are logged into more than one host:
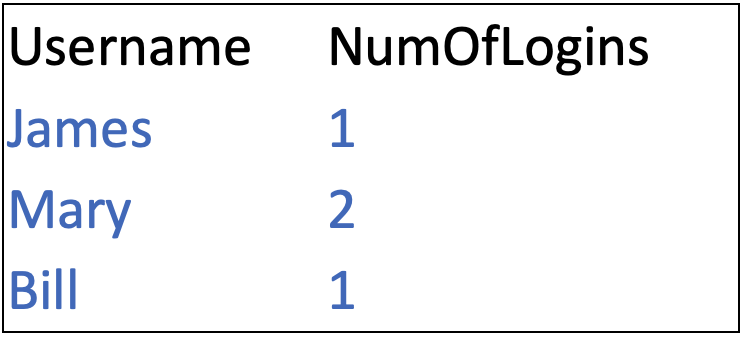
Conclusion
In this article, we discussed and illustrated the benefits of using the Splunk map command. It is another valuable tool at your disposal for correlating data and identifying relevant and crucial event patterns occurring on your systems and networks.






