Splunk Search Processing Language (SPL) serves as the nexus of Splunk’s data analysis capabilities. This powerful query language enables IT professionals, security analysts, and data scientists to search, analyze, and visualize machine-generated data in real time. Among these, the makemv command stands out as a particularly useful tool for transforming single-valued fields into multi-valued fields. As organizations collect increasing volumes of complex data, analysts frequently encounter information stored in concatenated strings or delimited formats. In such cases, the ability to split this information into multiple values becomes crucial for effective analysis.
Understanding the makemv Command
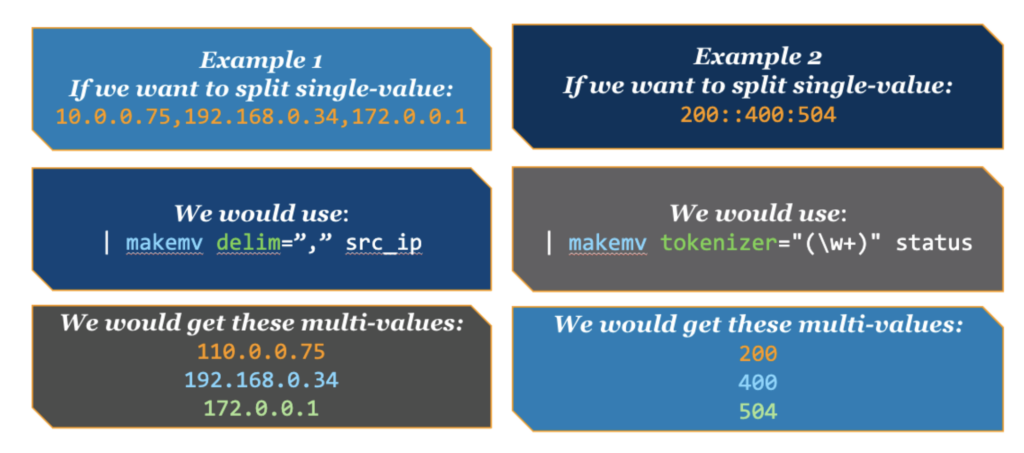
The makemv command fundamentally changes how Splunk interprets field values. When applied to a field, it transforms a single-string value into a multi-valued field by dividing the values based on a delimiter or regex. For instance, a comma-separated list of IP addresses stored in a single field can be converted into a multi-valued field where each IP address becomes a separate value. After using makemv, Splunk treats the field as a collection of distinct values rather than a single string. Consequently, commands like mvcount, mvindex, and mvexpand can be applied to further manipulate these multi-valued fields.
Syntax of the makemv Command
The syntax of the makemv command is:
| makemv [delim=<string>
| tokenizer=<string>] [allowempty=<boolean>] [setsv==<boolean>] <field>
Required Parameters:
- field: Specifies the field to convert into a multi-valued field. This parameter is mandatory and must reference an existing field in your dataset.
Optional Parameters:
- delim: Defines the delimiter character(s) used to split the field value. The default delimiter is a whitespace.
- allowempty: When set to true, empty values between delimiters are preserved as empty values in the resulting multi-value field. The default is false.
- tokenizer: When used instead of delimiter, you use regex to delimit your multi-values. This is great for more complex or uneven separation of values.
- setsv: This will combine the values into a single string that occupies the same field as the multi-values. The default is false.
To apply the makemv command effectively, you must position it appropriately in your search pipeline. It is recommended you keep in mind the change when using any calculation or transformation commands before and after.
Benefits of Using makemv in Daily Splunk Activities
Incorporating the makemv command into your Splunk workflow offers several significant advantages:
- Enhanced Data Exploration: Converting delimited strings into multi-valued fields allows for more intuitive data exploration, especially when working with lists of items like usernames, IP addresses, or event types. As a result, analysts can more easily identify patterns and relationships within complex datasets.
- Simplified Filtering and Statistical Analysis: After transforming fields with makemv, you can use Splunk’s powerful filtering capabilities to focus on specific values within these fields. Moreover, statistical functions can be applied to analyze the distribution and frequency of individual values within multi-valued fields.
- Improved Integration with Splunk’s Ecosystem: Many of Splunk’s advanced features and apps work more effectively with properly structured multi-valued fields. For example, the Enterprise Security app uses multi-valued fields extensively for threat intelligence and correlation searches.
Example Use Cases
Example #1: Analyzing Multiple Source IP Addresses
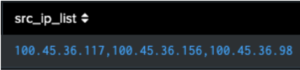
We can divide these up using makemv, changing them to multi-values:
index=network sourcetype=firewall
| makemv delim="," src_ip_list
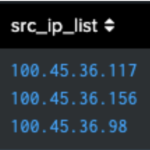
Explanation: This search performs several operations. First, it retrieves firewall logs from the network index. Then, the makemv command splits the src_ip_list field at commas, creating a multi-valued field. From here, we could expand these values out into their own events with mvexpand and then perform calculations on those values as they are now separated from one another.
Example #2: Analyzing User Roles from Active Directory Logs
Use Case: When working with Active Directory logs, user role information often appears as semi-colon delimited lists within the user_roles field.
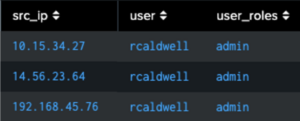
index=main sourcetype=active_directory user_action=login
| makemv delim=";" user_roles | search user_roles="Admin"
| stats count by user, src_ip
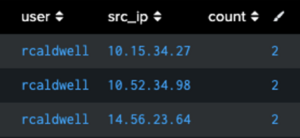
Example #3: Processing Values Unevenly Delimited
Use Case: You will sometimes get strings of values that do not have a similar delimitation between them.
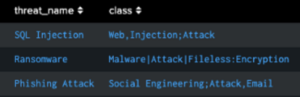
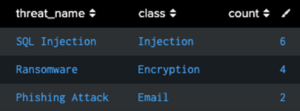
If we only want to capture what we want, we can use:
| datamodel Threat_Detection search
| fields threat_name, class
| makemv tokenizer="(\w+)" class
| mvexpand class
| stats count by class, threat_name
| sort -count
Conclusion
The makemv command represents an essential tool in any Splunk administrator’s or analyst’s toolkit. By transforming single-valued fields containing delimited data into proper multi-valued fields, this command unlocks powerful analytical capabilities and simplifies complex data exploration tasks.
To summarize the key points:
- The makemv command converts delimited strings into structured multi-valued fields, enabling more sophisticated analysis and visualization of complex data.
- Proper implementation of makemv requires careful consideration of delimiter choice, empty value handling, and positioning within the search pipeline.
- When combined with other multi-value field commands like mvexpand and mvcount, makemv facilitates deep analysis of relationships within complex datasets that would otherwise require extensive string manipulation.
By mastering the makemv command and incorporating it into your regular Splunk workflows, you can significantly enhance your data analysis capabilities and extract more valuable insights from your machine data.
To access more Splunk searches, check out Atlas Search Library, which is part of the Atlas Platform. Specifically, Atlas Search Library offers a curated list of optimized searches. These searches empower Splunk users without requiring SPL knowledge. Furthermore, you can create, customize, and maintain your own search library. By doing so, you ensure your users get the most from using Splunk.






