Data fields that have similar information can have different field names. While the Splunk Common Information Model (CIM) exists to address this type of situation, it is not always utilized. By using the coalesce command you can create a new field that contains the information from both fields and insert a value if no information exists.
What is the Splunk coalesce Command?
The definition of coalesce is “To come together as a recognizable whole or entity”. In the context of Splunk fields, we can look at the fields with similar data in an “if, then, or else” scenario and bring them together in another field. The Splunk Search Processing Language (SPL) coalesce function takes one or more values and returns the first value that is not null.
The Benefits of Splunk coalesce Function
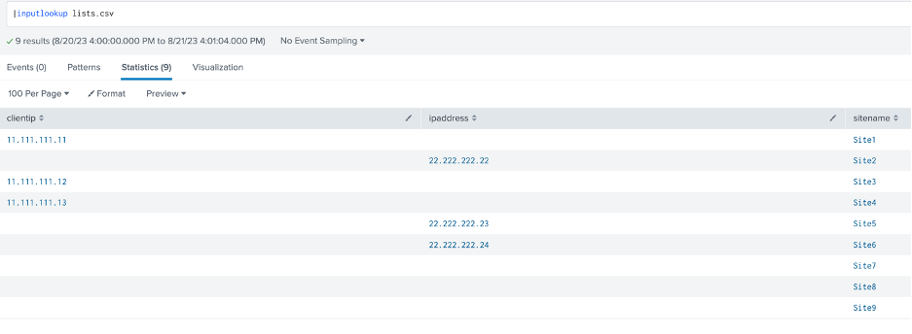
Consider the following lookup table:
Some of the sites have their IP address fields as “clientip” and other sites as “ipaddress”, with several not having that information. To mark this information into a single field name, the coalesce function can easily be utilized through the “eval” function.
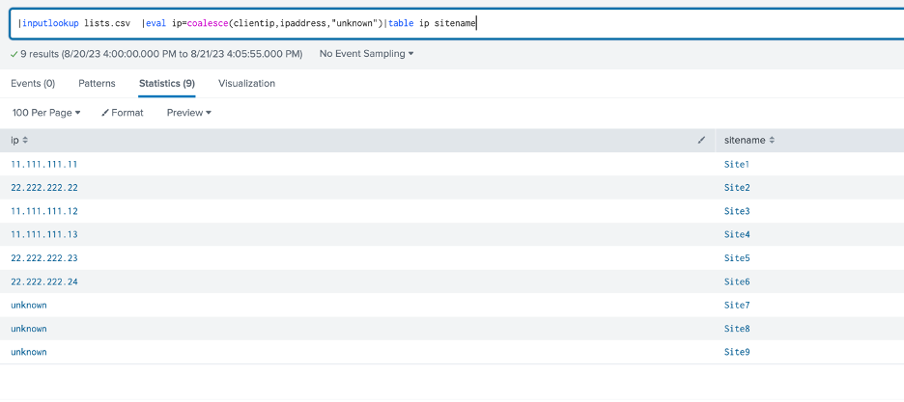
Let’s create a new field named “ip”:
if the site has a “clientip” field, place the “clientip” value into the “ip” field
if the site does not have a “clientip” field but has an “ipaddress” field, place the “ipaddress” value into the “ip” field
if the site has neither of the fields, place the static value “unknown” into the “ip” field
The SPL function syntax is:
| eval ip=coalesce(clientip,ipaddress,”unknown”)
The information for each site’s ip address is now in a common ‘ip’ field whether the address is present or unknown:
Conclusion
The coalesce function allows users to view data from different, but similar, fields in a common field along with options to notate if data is available or unknown. The utilization of this function gives users the ability to provide consistent information and alert stakeholders of situations where information is not known.