A Splunk search can result in a return dataset that can be overwhelming in both visual and time-consuming aspects. The “| head” or “| tail” command can be used to limit the number of results a user will see as well as to quickly find and identify fields of interest.
What is the Splunk Head/Tail Command?
The head command returns a specified number of results in search order, starting with the most recent based on _time. The default number of results is 10, but this can be changed by specifying the desired number after the command.
The tail command works similarly to the head command, only, it returns the last sequence of events in search order, again based on _time.
Both head and tail commands allow the user to view a select few of the thousands of events that can result from a Splunk search.
The Benefits of Splunk Head/Tail Command
The head and tail commands significantly reduce the number of returned results, allowing the user to quickly view a sample of the dataset, and providing quick oversight of the various fields present in a given index and sourcetype. A field of interest can be further analyzed by leveraging a cousin to the head and tail commands – the | top <field> command. The | top <field> command will return the count and percentage of the specified field(s).
Another benefit of the head or tail command is the time savings combined with the number of records that Splunk will scan. Here’s an example of a search using the head (or tail) command vs. a search that is not using it:
With the head command, 5 results were returned by scanning 51 events in 2.276 seconds:
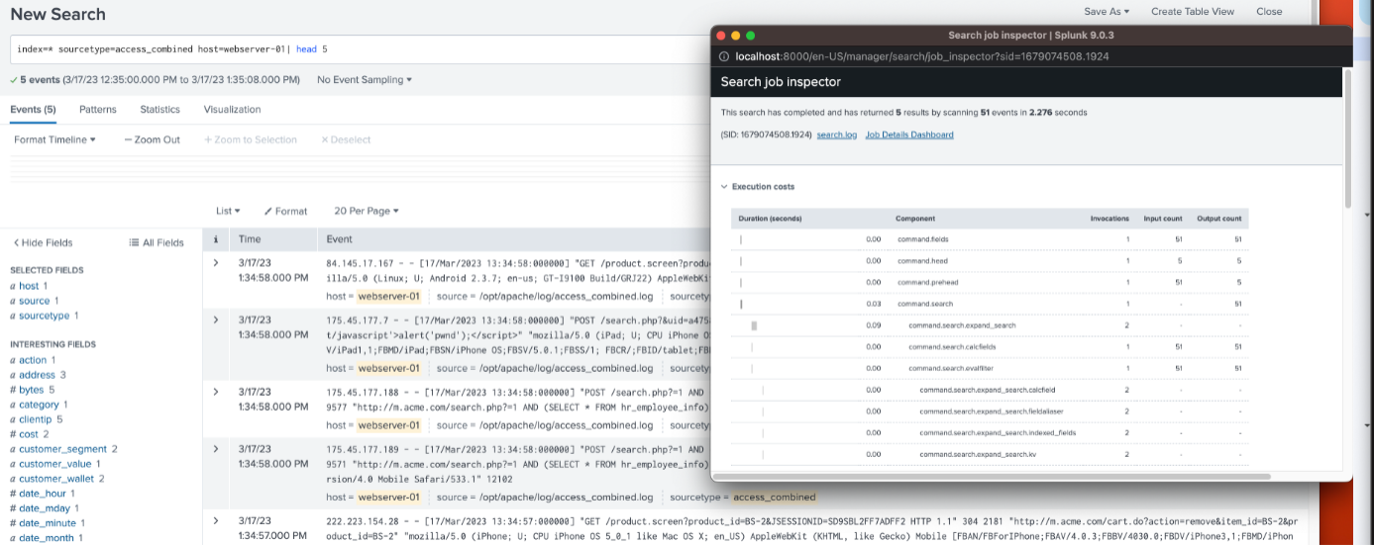
Without the head command, 4,269 events were returned by scanning 4,271 events in 3.095 seconds:
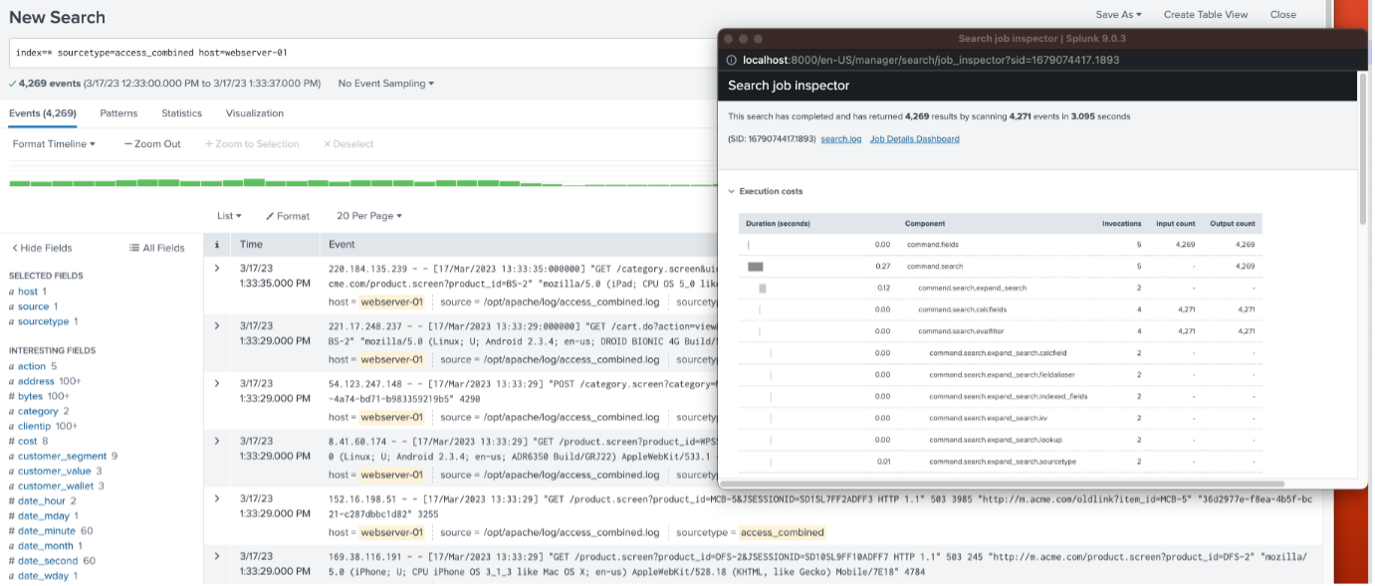
The number of scanned events is drastically lower using the head command and will depend on the time range selected, which was 60 minutes for both searches.
How to use the Head and Tail Commands
Let’s start with the head command. The SPL below will display the first five (5) events from a search; note the use of the pipe ‘|’ in front of the head command:
Index=* host=webserver-01| head 5

The first 5 events are displayed as found in the search order, which is based on _time.
Another example would be to examine the first 5 results of the number of bytes between a webserver and target client’s IP’s.
The initial search without any result constraints:
index=web host=webserver-01 | stats sum(bytes) as Bytes by clientip
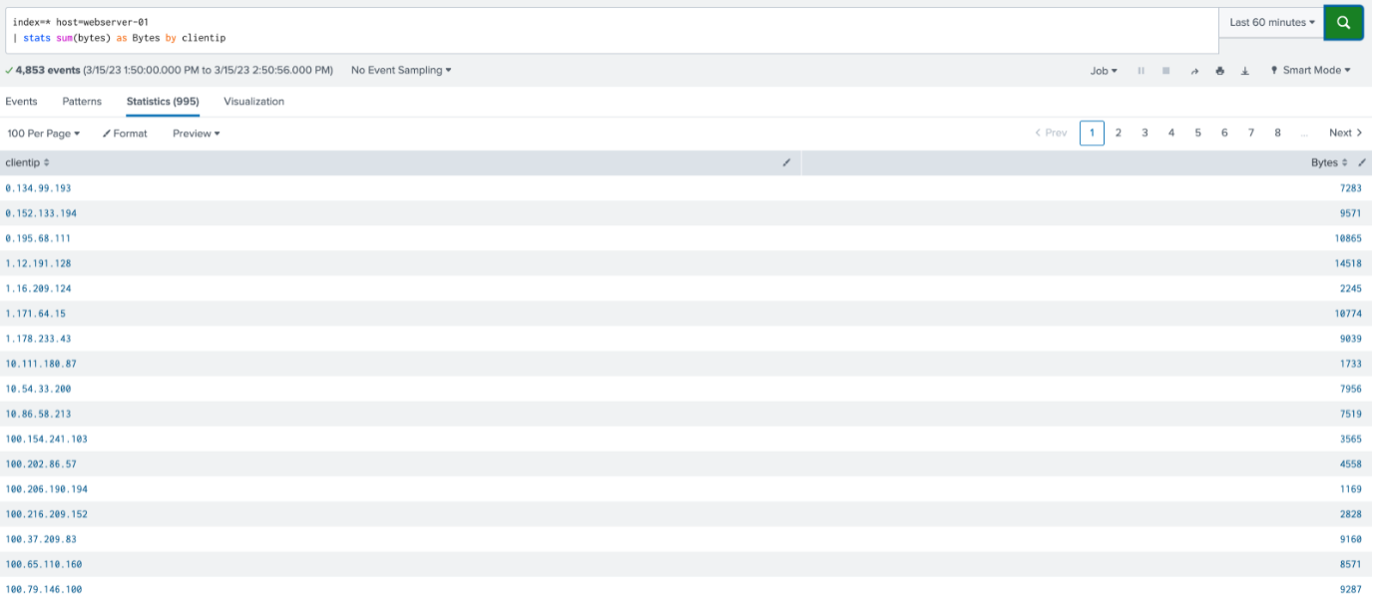
The result is 995 different client IP’s. If the user would only want to see the first five (5) results, in search order, the “| head” statement can be utilized as follows:
index=web host=webserver-01 | stats sum(bytes) as Bytes by clientip | head 5
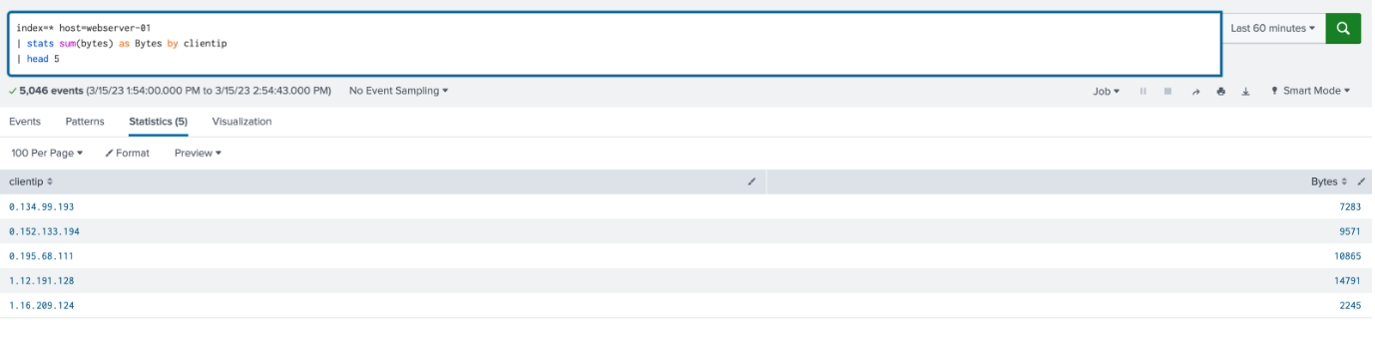
The first five results that the search finds will be present in the table.
If the desired result set is 15:
index=web host=webserver-01 | stats sum(bytes) as Bytes by clientip | head 15
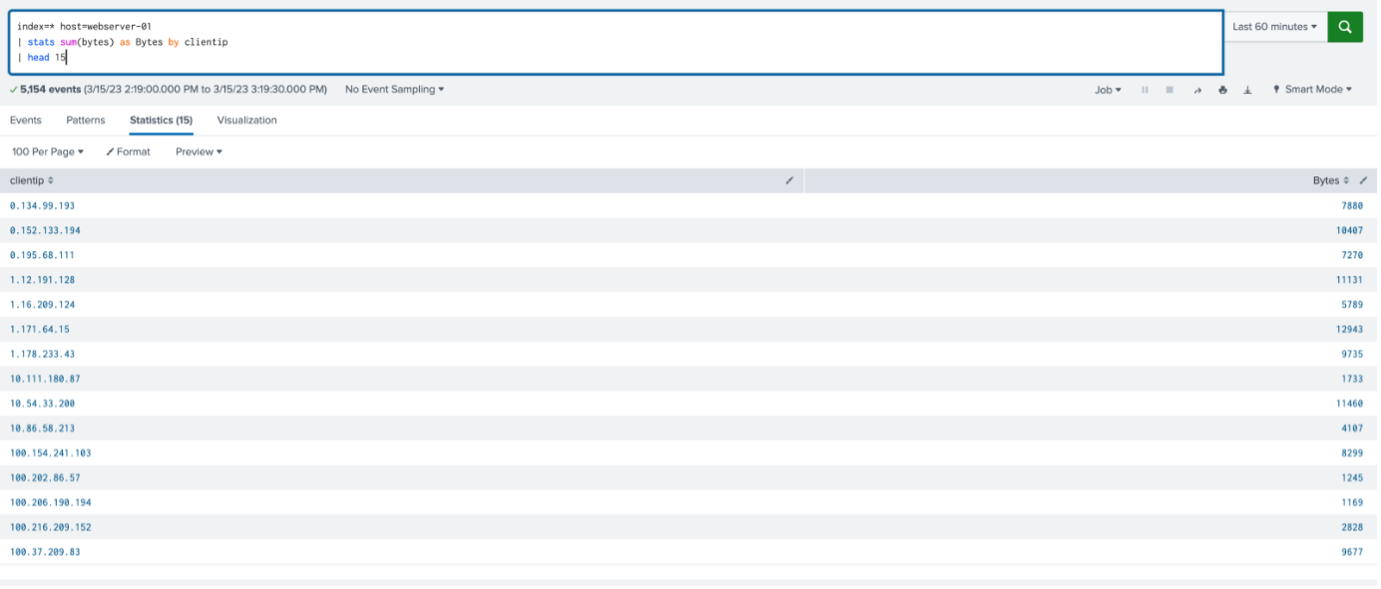
The first 15 results that the search finds will be present in the table.
If no integer is defined in the “| head” statement, it returns ten (10) results, if they exist, by default:
index=web host=webserver-01 | stats sum(bytes) as Bytes by clientip | head
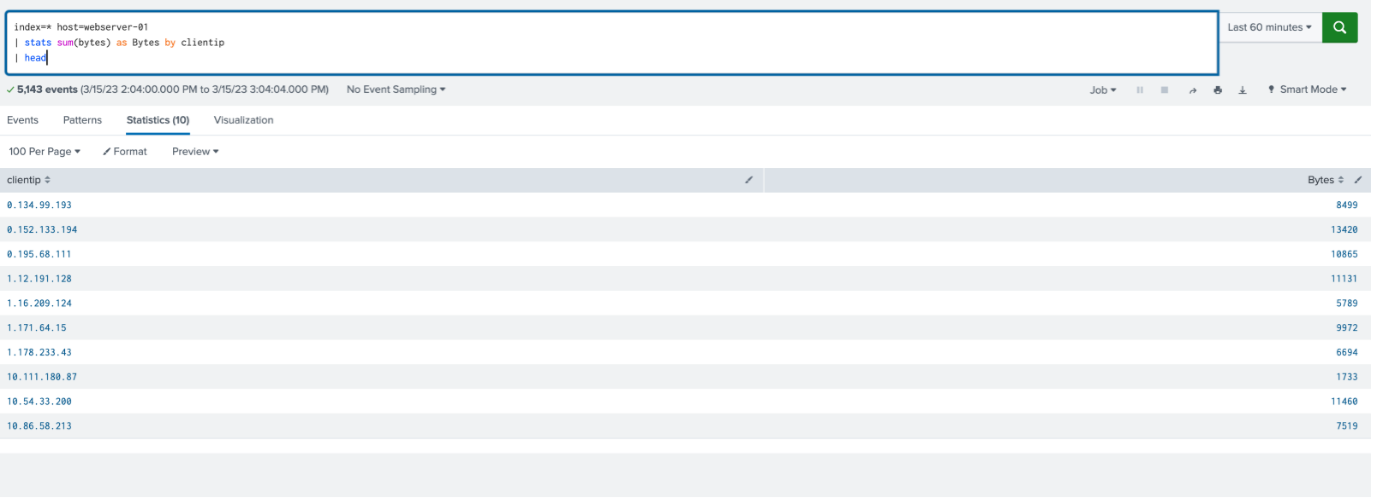
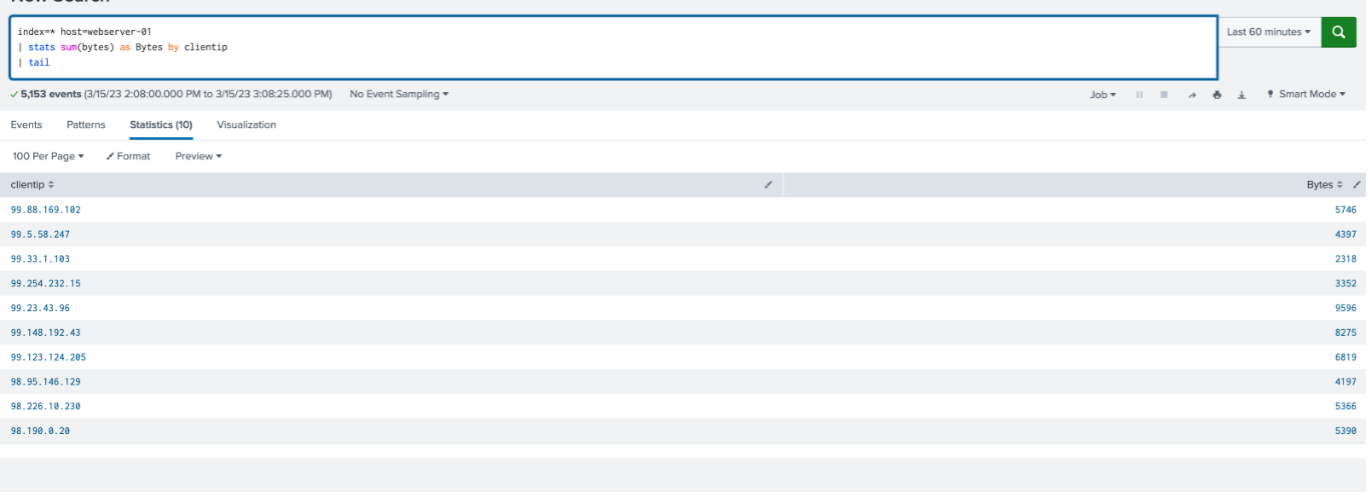
Conversely, the | tail command works for the last 10 results in the search order, with the default value of ten (10):
index=web host=webserver-01 | stats sum(bytes) as Bytes by clientip | tail
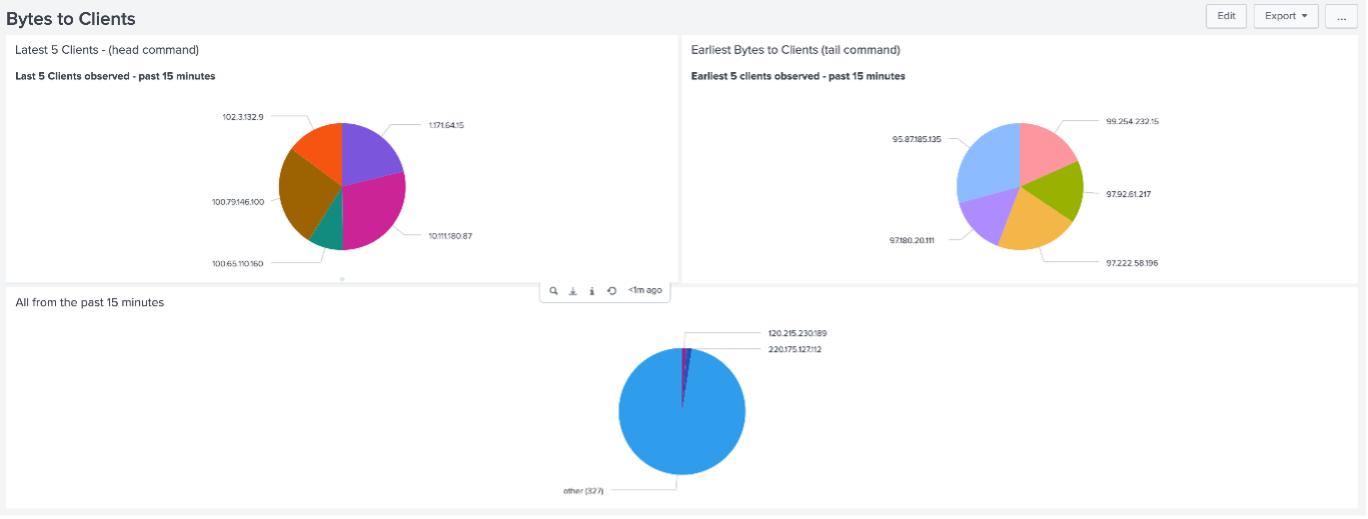
Example of use – Pie Chart
The following Pie Chart demonstrates how to utilize the head and tail commands in a useful visualization.
The bottom panel displays the result of a search of all Client IP addresses that are receiving information to and from the Webserver. Since there are many clients, the search does not render an accurate result of the information an end-user might be looking for.
The top-left panel utilizes the “| head 5” command, displaying the latest 5 client results. In contrast, the top-right panel utilizes the “| tail 5” command showing the earliest 5 client results.
Conclusion
The head and tail commands allow users to view a user specified number of events at the beginning and/or end of a time range in a Splunk search. The utilization of these commands gives users the potential to minimize compute resource usage by reducing the number of records that are scanned and obtaining a quick summary of the dataset.
If you found this helpful…
You don’t have to master Splunk by yourself in order to get the most value out of it. Small, day-to-day optimizations of your environment can make all the difference in how you understand and use the data in your Splunk environment to manage all the work on your plate.
Cue Atlas Assessment: Instantly see where your Splunk environment is excelling and opportunities for improvement. From download to results, the whole process takes less than 30 minutes using the button below: