Working in the security space in Splunk, we’re all accustomed to the pressure of security alert management, and security analysts are on the front line of security alert responding. Repeated exposure to alerts can result in “alert fatigue” — monitoring an abundance of alerts ad nauseam.
When your security alerts are too frequent, not descriptive enough, or redundant, this kind of fatigue can leave teams even more exposed to legitimate threats. Put simply, your Splunk environment can start to take on characteristics of the fable, The Boy Who Cried Wolf, and we know how that story ends.
And we don’t want that for your team. In this post, we’ll show you how to avoid alert fatigue with Splunk Event Sequencing.
What is Event Sequencing?
The Event Sequencing engine is a series of chained (sequenced) correlation searches. These searches are triggered based on search criteria and other modifiers. Once the conditions of all sequenced correlation searches are met, a sequenced event that includes all the alert data is generated. Analysts can use this data to make decisions about how to triage alerts.
The best function of Event Sequencing is that it can identify the actionable threats amidst the sea of alerts you receive each day. Using Event Sequencing leads to quicker remediation of security incidents.
How Event Sequencing Works in Splunk
Let’s take a look into how Splunk Event Sequencing works. Sequenced Events start by creating a Sequence Template. With Event Sequencing, out-of-the-box correlation searches, or custom searches, can be used.
You can create the sequencing template to detect specific behavior that an analyst can take immediate action upon. You can follow these graphics below for further reference to creating your sequence templates.
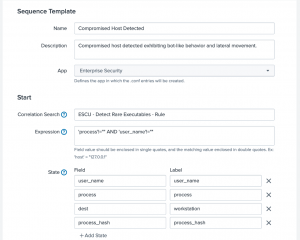
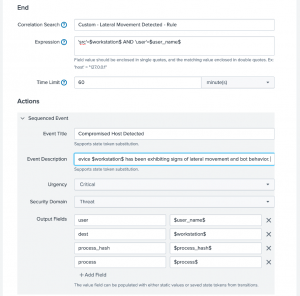
After the sequence template is created, you will find the triggered events in the Incident Review.
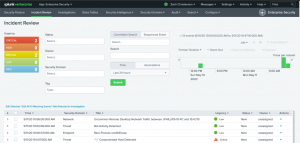
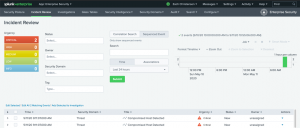
Then, you’ll want to filter your events. Click to filter on your “Sequenced Events” for these specific events.
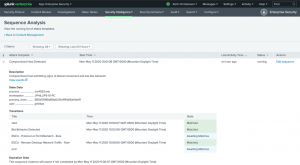
Once you run your sequenced events, find them at Security Intelligence > Sequence Analysis. Then, you can review your sequence analysis.
Threats Minimized, Efficiency Maximized
When you take these best practice tips to Splunk Enterprise Security, your security alerts should be more manageable and consumable. Splunk Event Sequencing is here to help and ensure your Splunk teams are efficient and successful in the security space. With a team of security experts, Kinney Group has years of experience working in Splunk to ensure threats do not slip through the cracks. If you’re interested in our work with Splunk Enterprise Security, let us know below!